Authentication Events
Description: Authentication mechanisms.
Location:
- C:\Windows\System32\winevt\logs\Security.evtx
Notes: Authentication mechanisms related to NTLM and Kerberos protocols:
Event ID Codes for NTLM:
- Event ID: 4776 - Successful/Failed account authentication.
Event ID Codes for Kerberos:
- Event ID: 4768 - Ticket Granting Ticket was granted. (Successful Logon)
- Event ID: 4769 - Service Ticket requested. (Access to Server Resource)
- Event ID: 4771 - Pre-authentication failed. (Failed Logon)
Analysis: NTLM and Kerberos are the primary authentication protocols utilized in a Windows
envirornment. NTLM is a challenge-response-based authentication protocol used by Windows computers that are
not members of an Active Directory domain. Kerberos is a ticket-based authentication protocol used by
Windows computers that are members of an Active Directory domain. For some more reading material that deep
dives on the subject, I'd recommend this blog post from Ultimate Windows
Security.
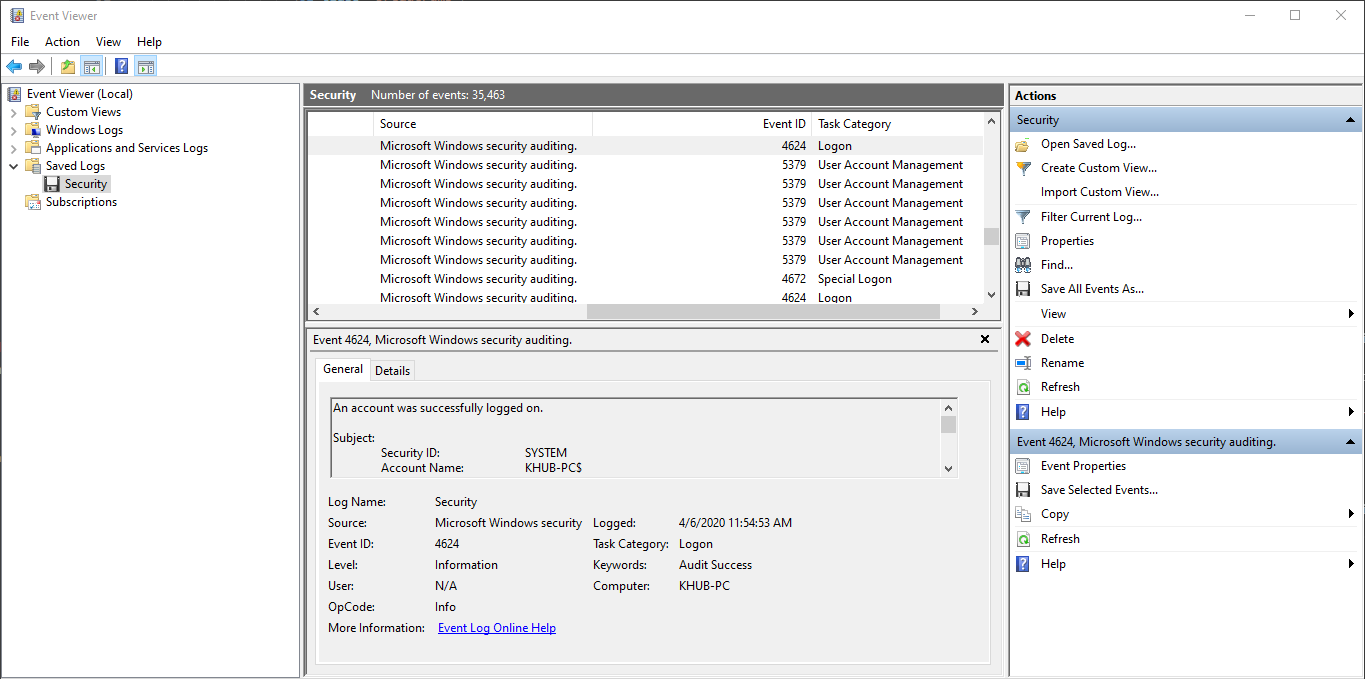
We can use Windows native Event Viewer application for analyzing .evtx files. On a Windows client,
double-clicking an .evtx file will automatically open the log inside of the Saved Logs
folder in Event Viewer.
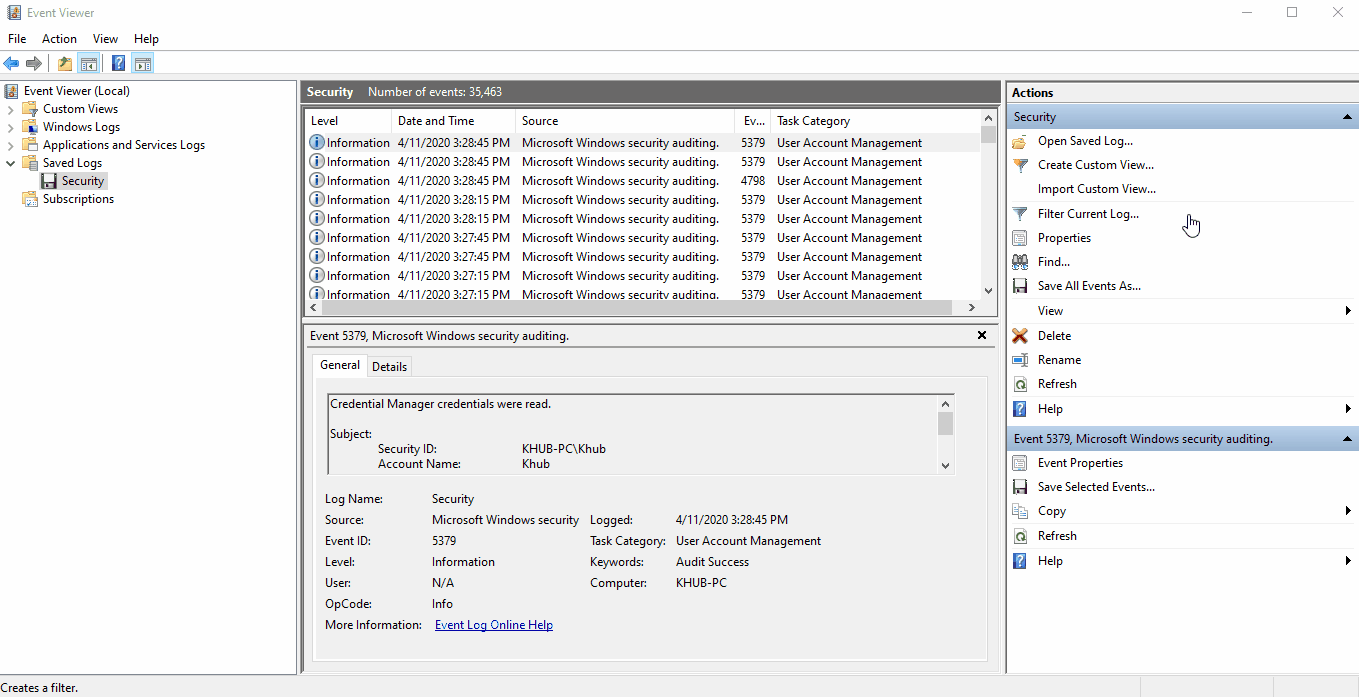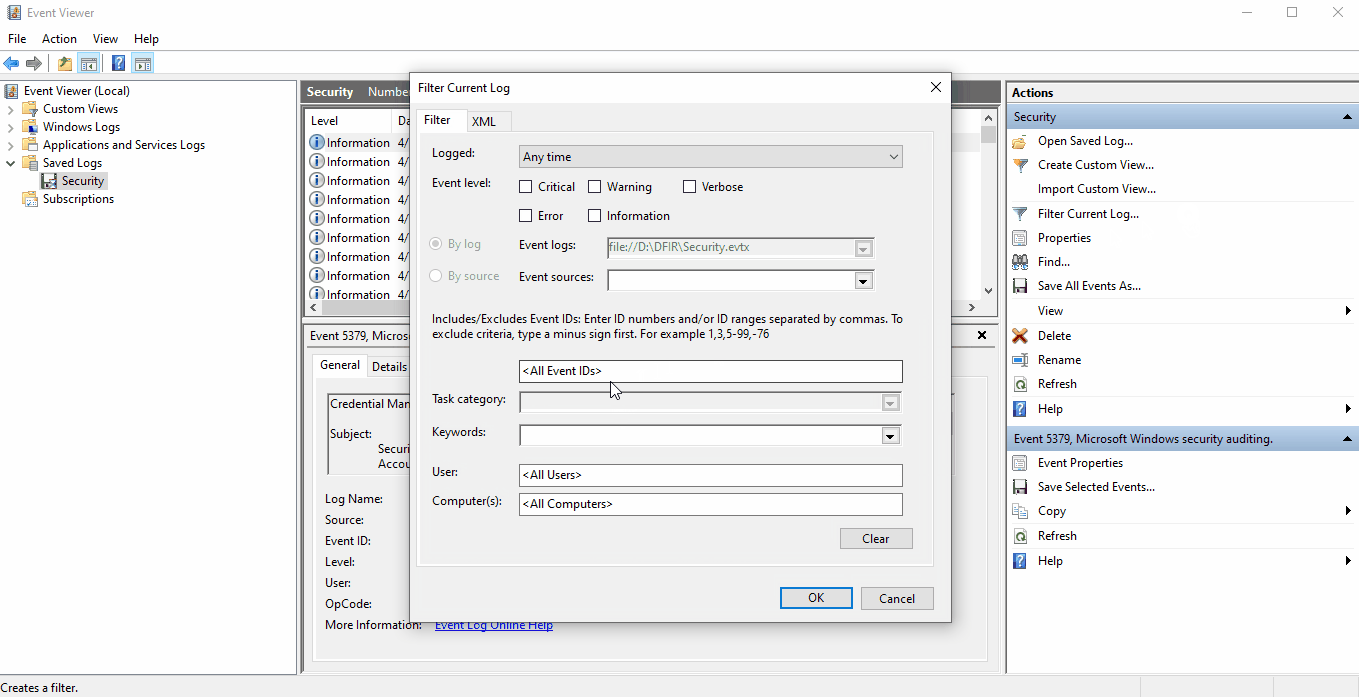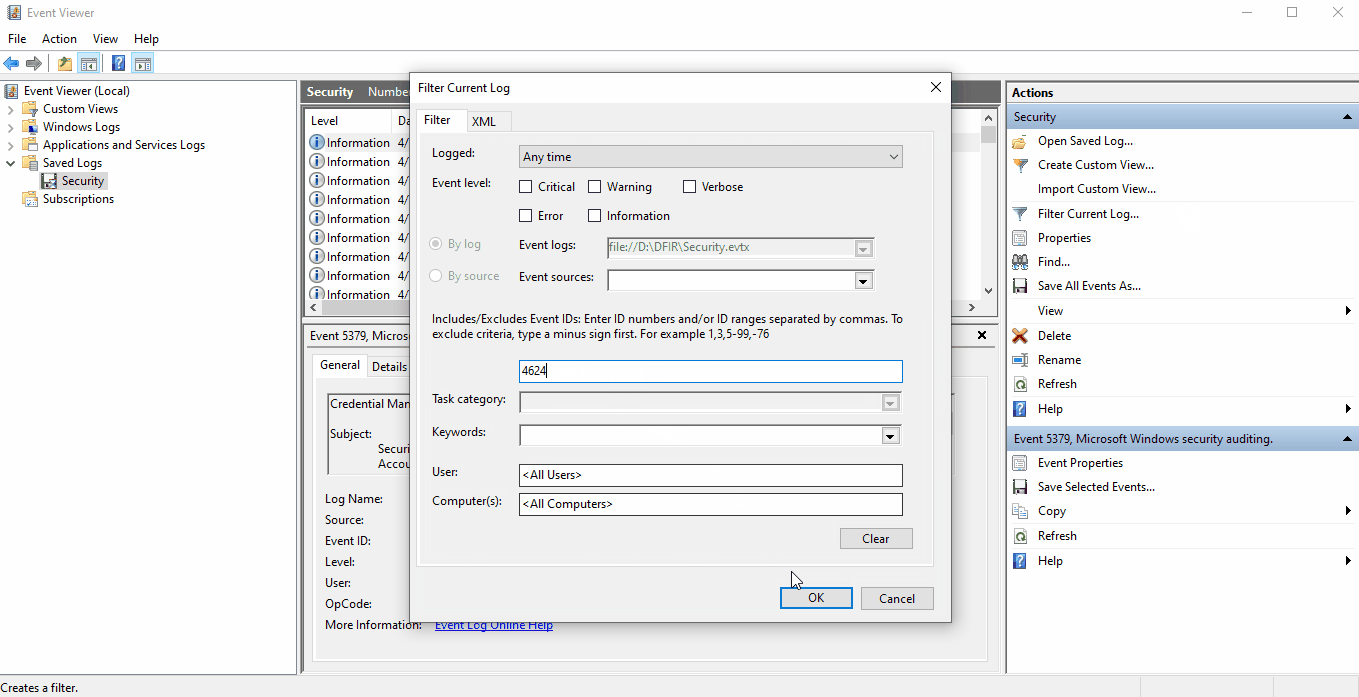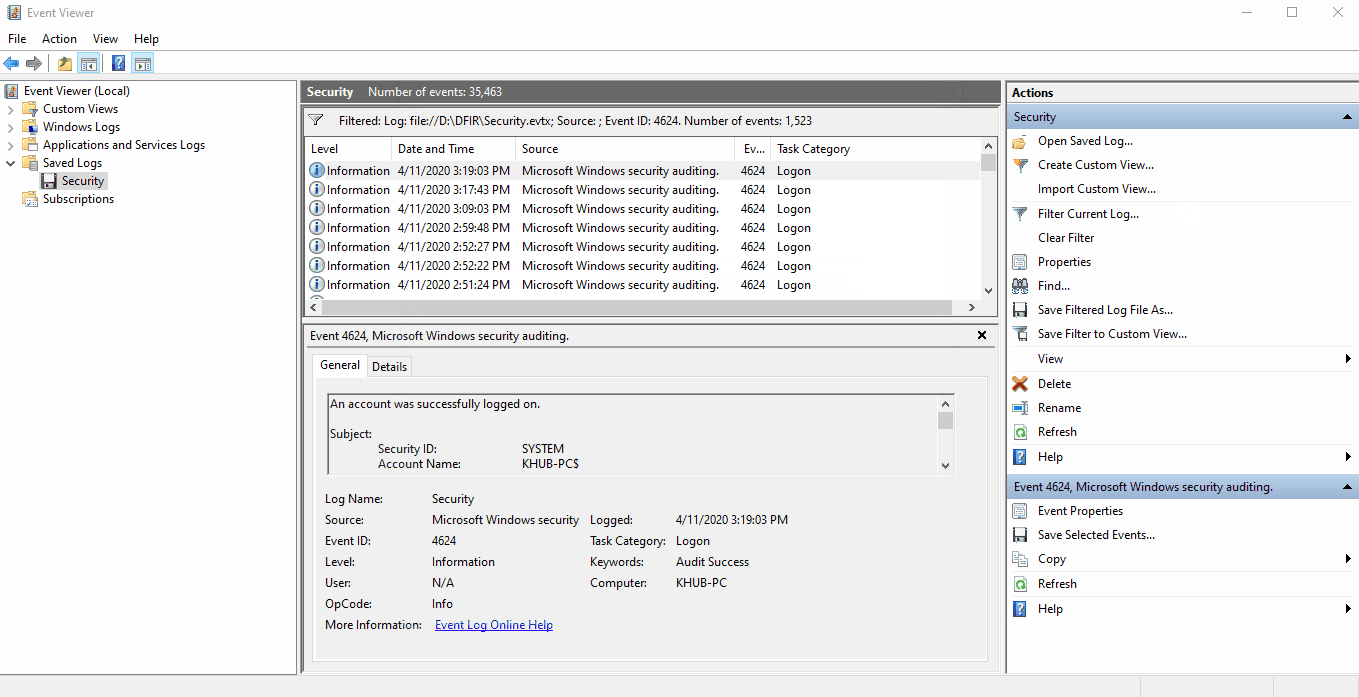
To filter for a specific event, select Filter Current Log... to pull up a dialog box with
filtering option and input the Event ID you'd like to isolate.
I don't currently have any examples of Kerberos authentication that I can showcase for reference, but I'm
working on setting up a small Windows environment for an upcoming Windows Forensics workshop and should be
able to capture client/server communications from that enviornment once it's up and running.