Logon Types
Description: Logon Events can give us very specific information regarding the nature of account authorizations on a system if we know where to look and how to decipher the data that we find. In addition to telling us the Date, Time, Username, Hostname, and Success/Failure status of a logon, Logon Events also enables us to determine by exactly what means a logon was attempted.
Location:
- C:\Windows\System32\Winevt\Logs\Security.evtx
Notes:
- Event ID: 4624 - An account was successfully logged on.
| Logon Type | Explanation |
|---|---|
| 2 | Logon via Console |
| 3 | Network Logon |
| 4 | Batch Logon |
| 5 | Windows Service Logon |
| 7 | Credentials used to Unlock Screen |
| 8 | Network Logon sending Credentials |
| 9 | Different Credentials used than Logged on User |
| 10 | Remote Interactive Logon (RDP) |
| 11 | Cached Credentials used to Logon |
| 12 | Cached Remote Interactive (Similar to Type 10) |
| 13 | Cached Unlock (Similar to Type 7) |
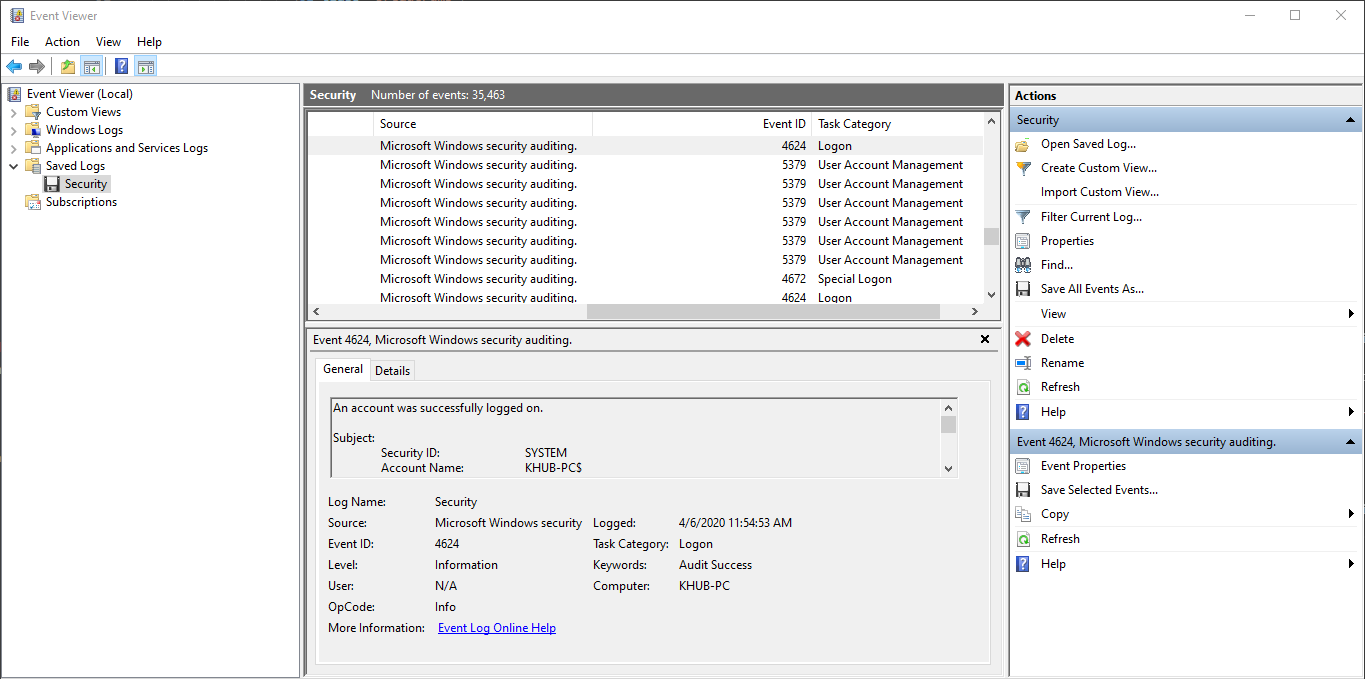
Analysis: The security.evtx log generates a 4624 event for every successful logon attempt
to the local computer. This event isn't limited to when an end user logs into their workstation from a
console but also includes authentication events via other mechanisms. Windows Service Logons inparticular
tend to generate a large number of 4624 events.
We can use Windows native Event Viewer application for analyzing .evtx files. On a Windows client,
double-clicking an .evtx file will automatically open the log inside of the Saved Logs
folder in Event Viewer.
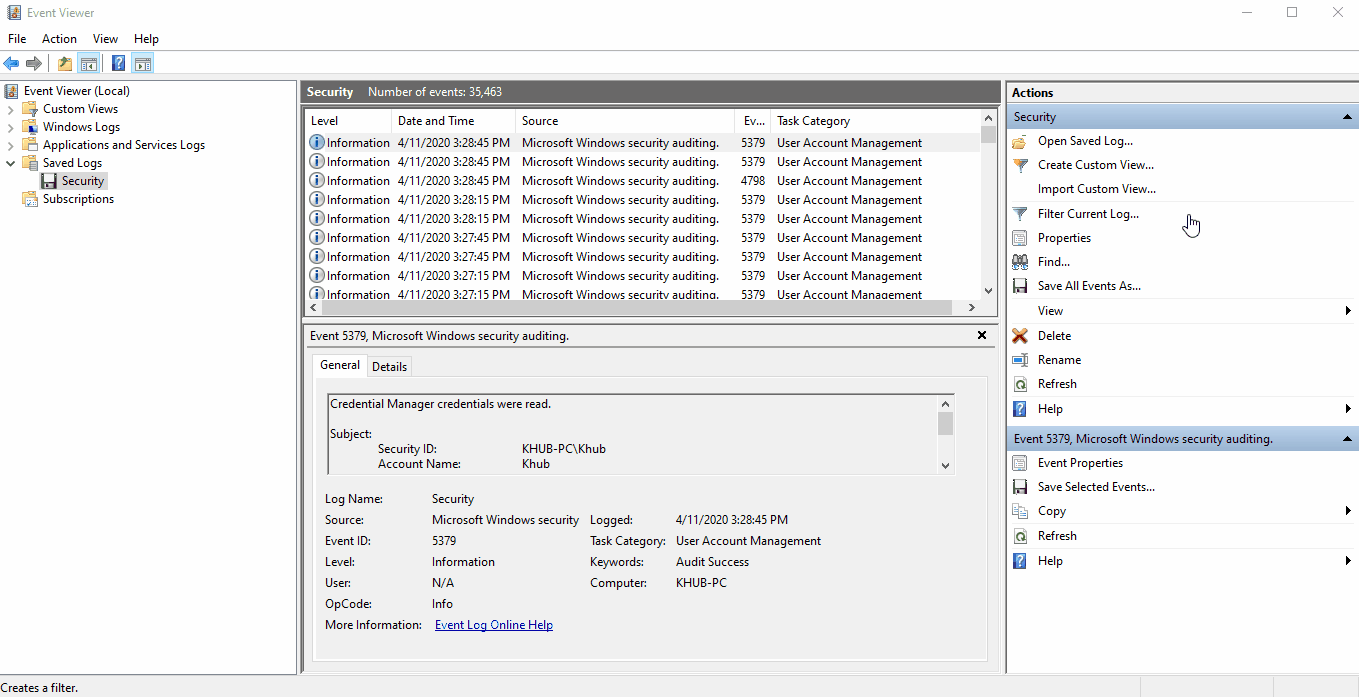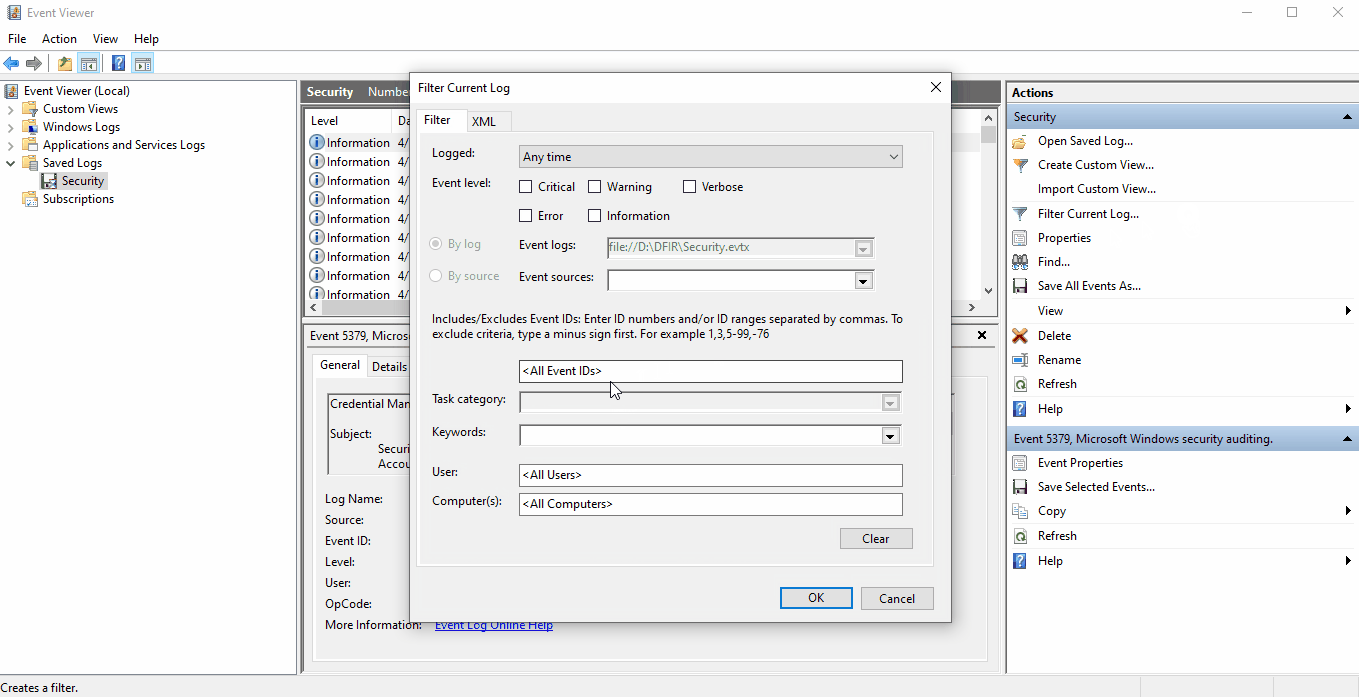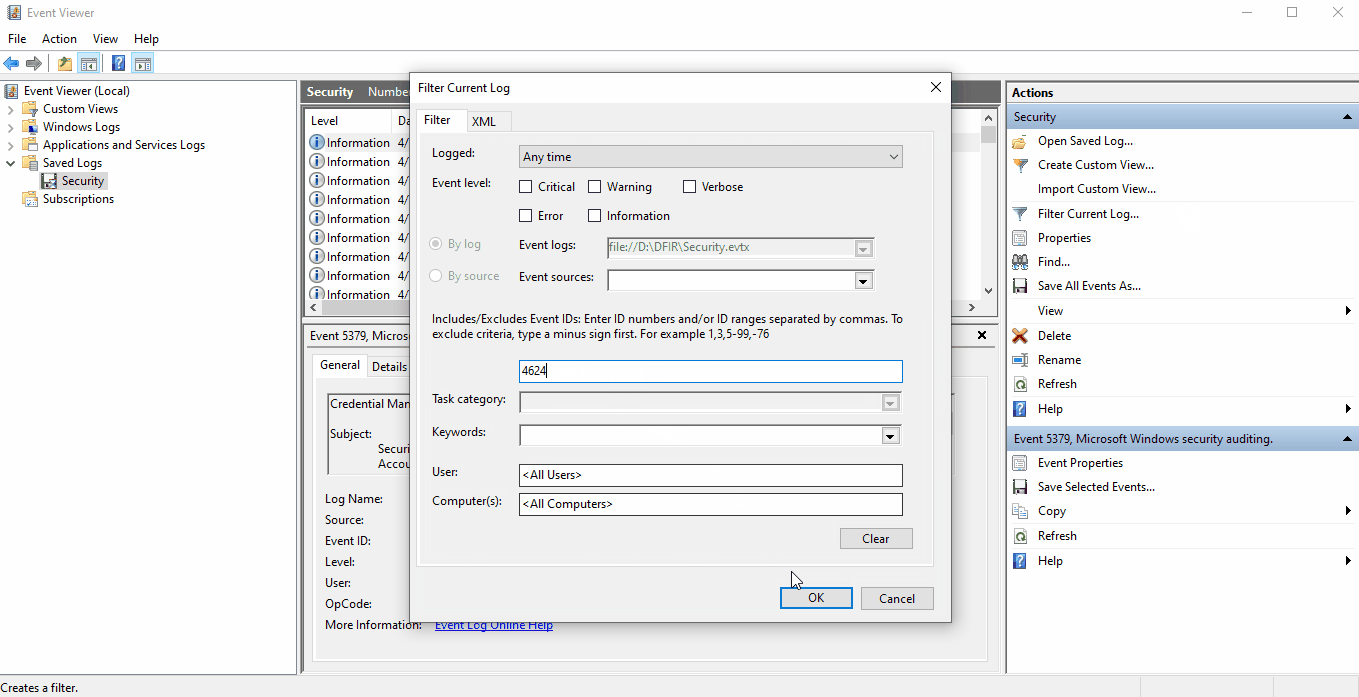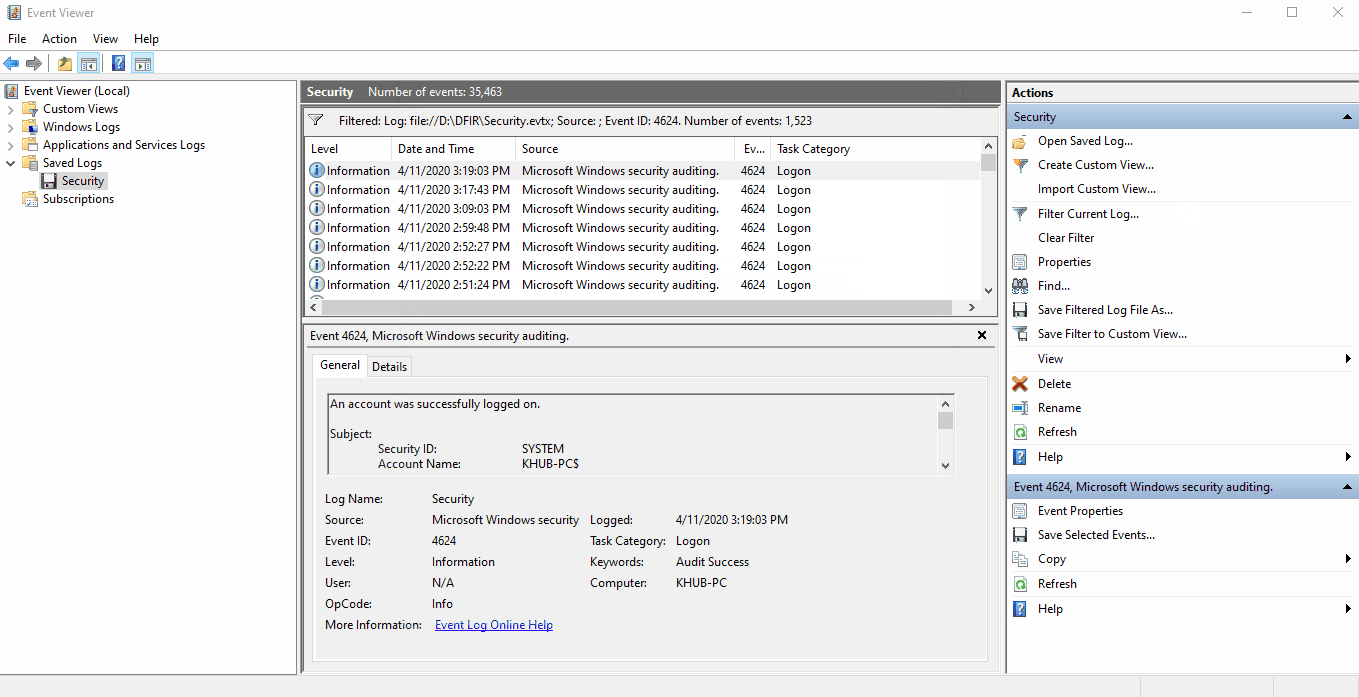
We can filter the security.evtx log to only show 4624 events by selecting Filter Current
Log... and inputing 4624 in the text box labled <All Event IDs>.
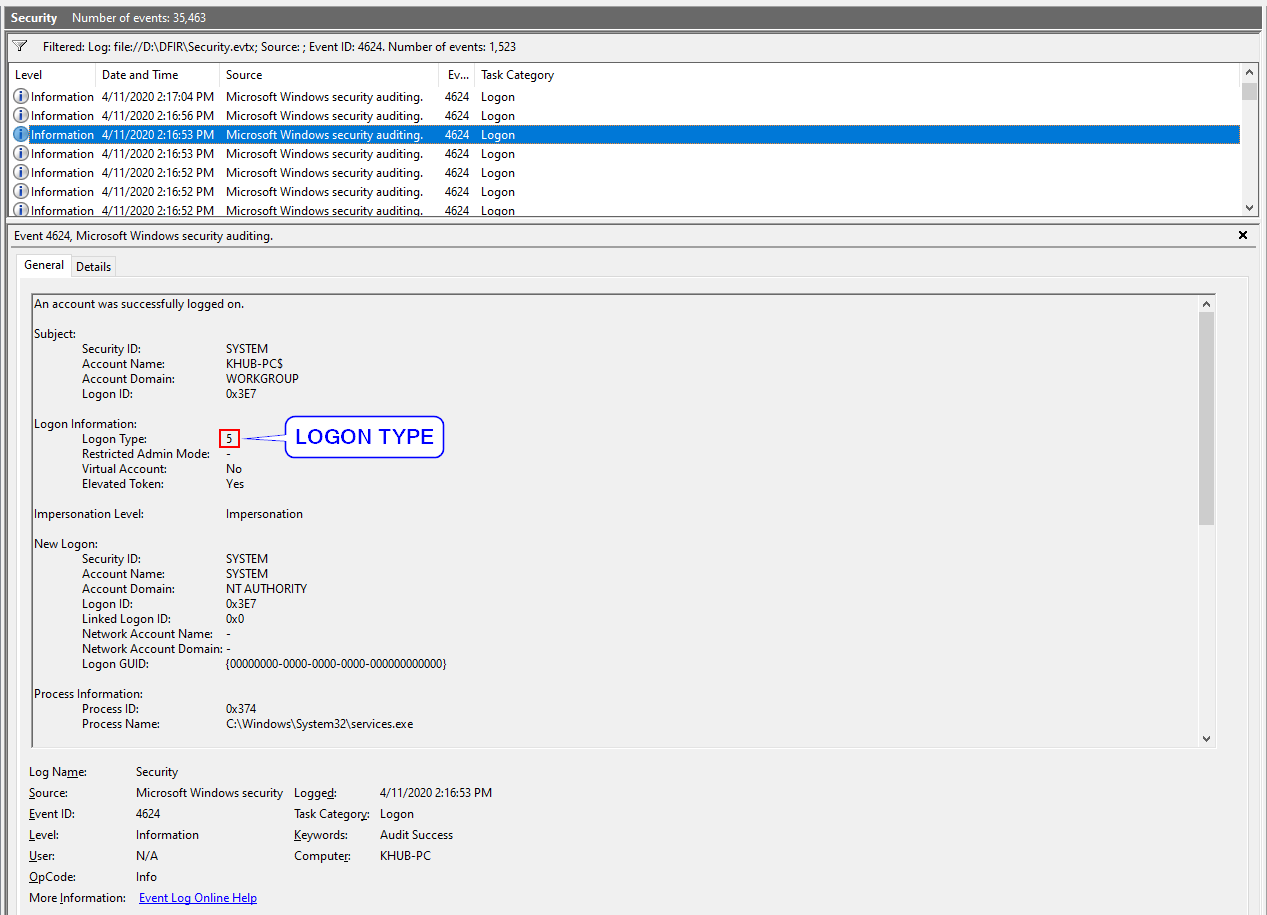
We can determine how a logon was attempted by reviewing the decimal value of Logon Type. In
the example below, the we can see that we're reviewing a Windows Service Logon.
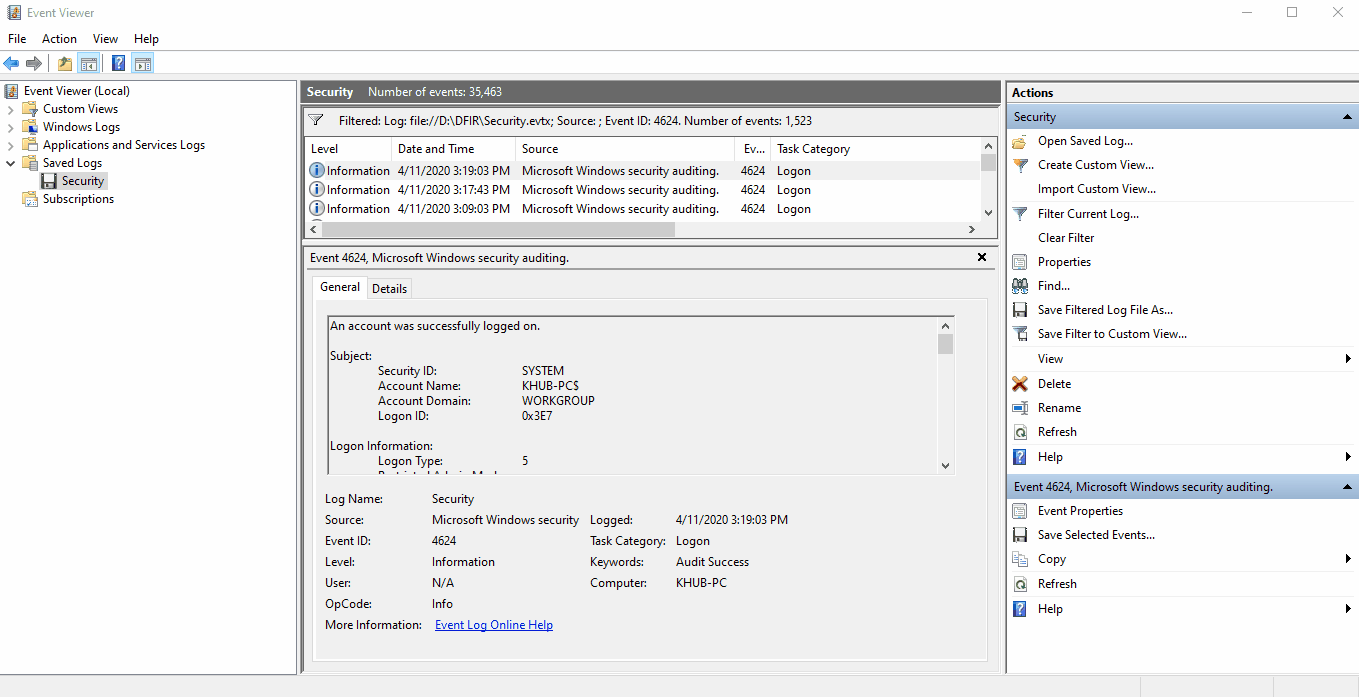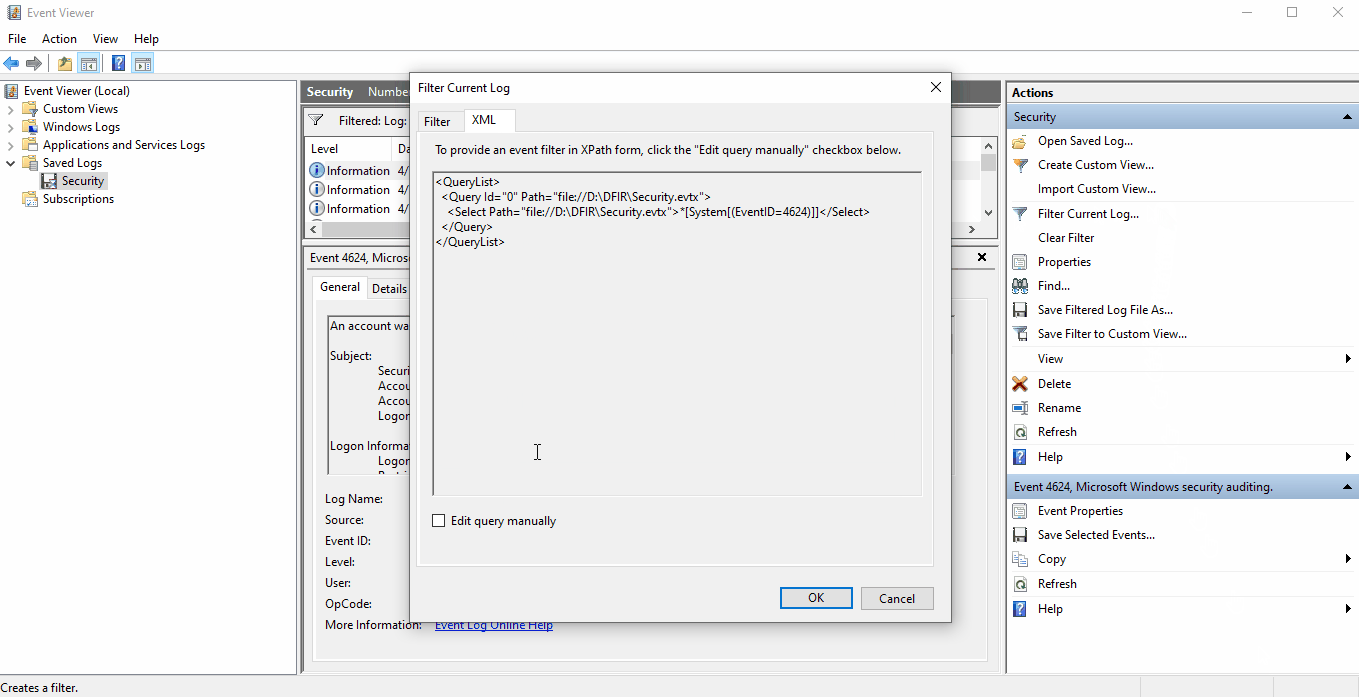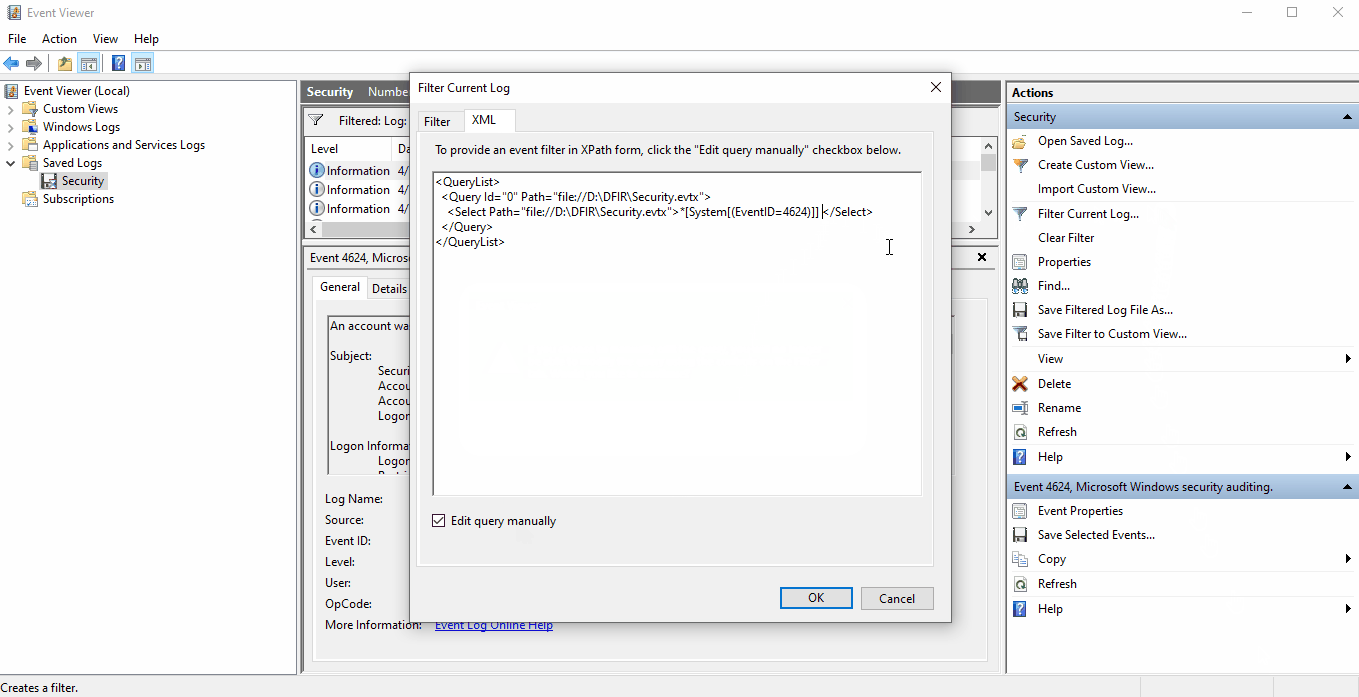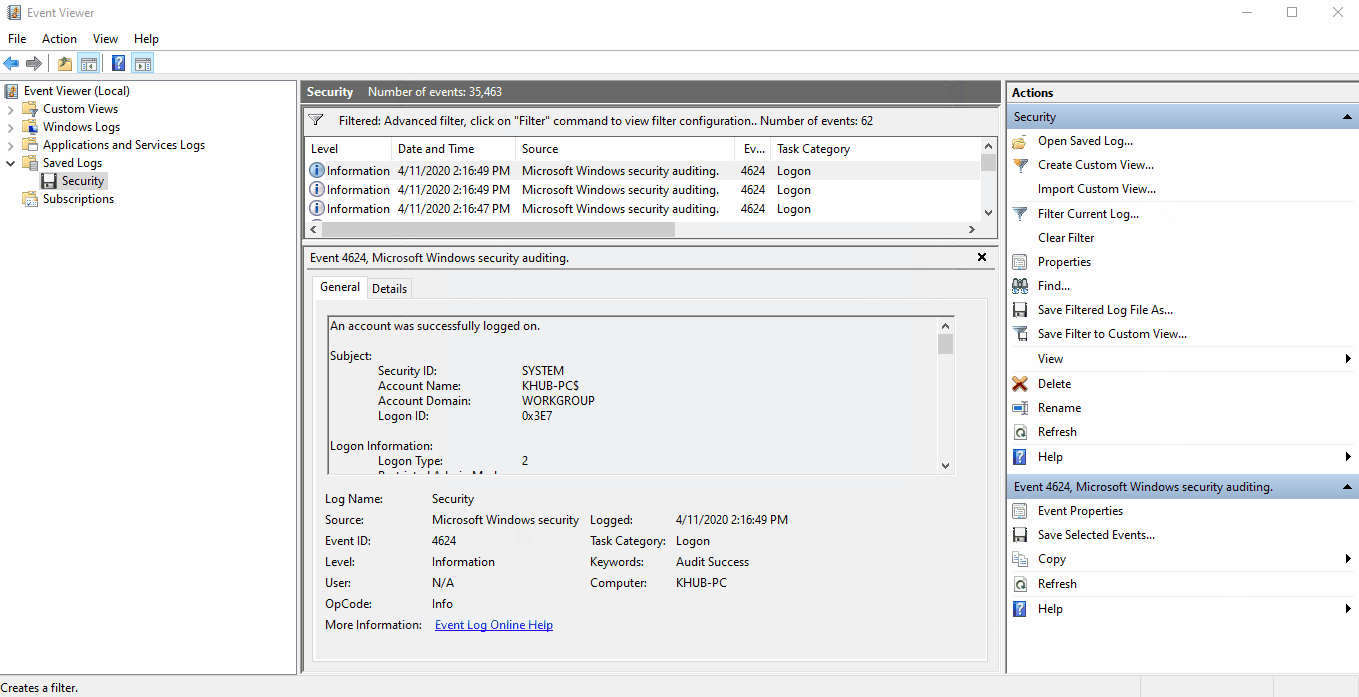
In many circumstances, we're only interested in viewing information for a specific type of logon. The
default filtering options within Event Viewer don't natively provide that type of granularity, so well need
to manually edit our search query using XML. To filter by a specific logon type: Modify your filter to only
show 4624 events --> Select Filter Current Log... -->
Select the XML tab --> Click the checkbox next to Edit query
manually --> Select Yes to accept the warning prompt
--> Copy and *[EventData[Data[@Name='LogonType'] and (Data='2')]] and
paste it right after your initial select statement *[System[(EventID=4624)]]
--> Select Ok. Modify the decimal value of Data as needed
for your query.