RDP Usage
Description: Track internal and external Remote Desktop Protocol connections.
Location:
- C:\Windows\System32\winevt\logs\Security.evtx
- C:\Windows\System32\winevt\logs\Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
Notes: The Security.evtx log can be used to track outgoing RDP connections:
- Event ID: 4624 - Logon Type 10
- Event ID: 4778 - Session Connected/Reconnected
- Event ID: 4779 - Session Disconnected
The Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx log can be used to track incoming RDP connections:
- Event ID: 1149 - Network Authentication Succeeded
Analysis: Attackers often use legitmate Windows tools to laterally traverse throughout an
enviornment. As a result, it's important to understand the forensic artifacts associted with RDP. There are
multiple Windows Event ID's associated with RDP and we often have to reference multiple logs to map out the
full picture.
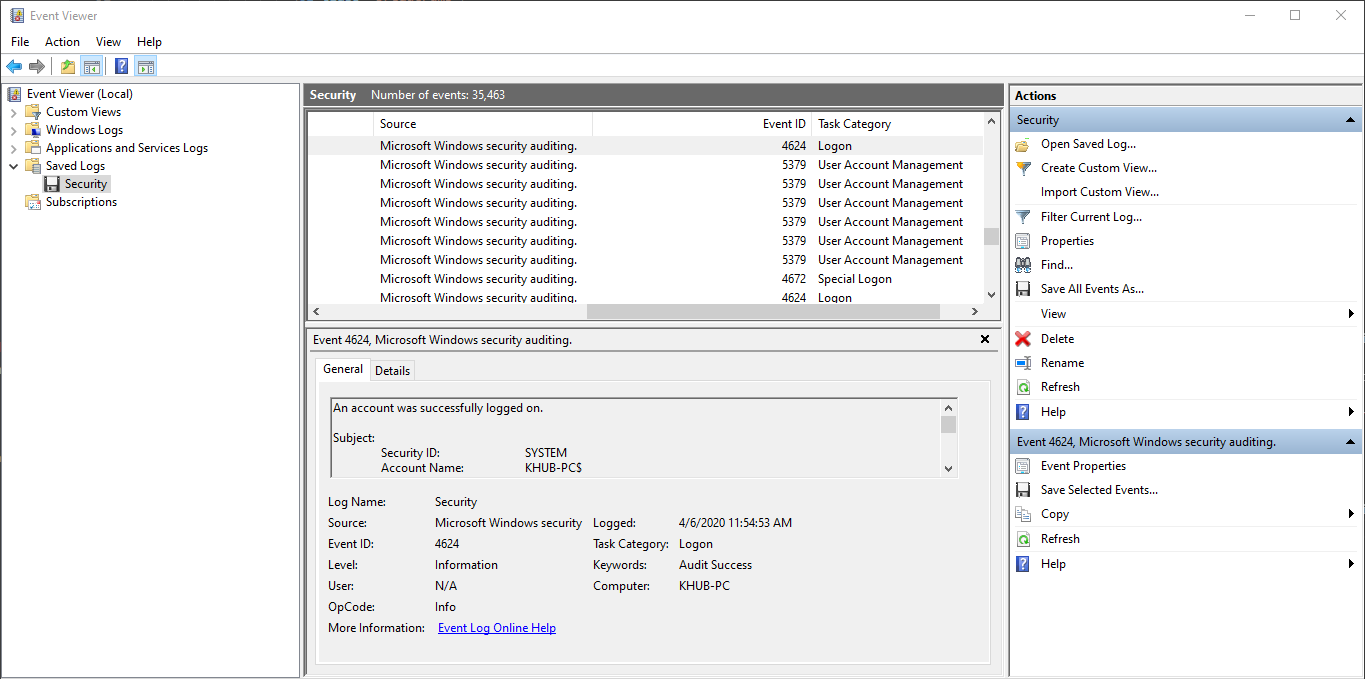
We can use Windows native Event Viewer application for analyzing .evtx files. On a Windows client,
double-clicking an .evtx file will automatically open the log inside of the Saved Logs
folder in Event Viewer.
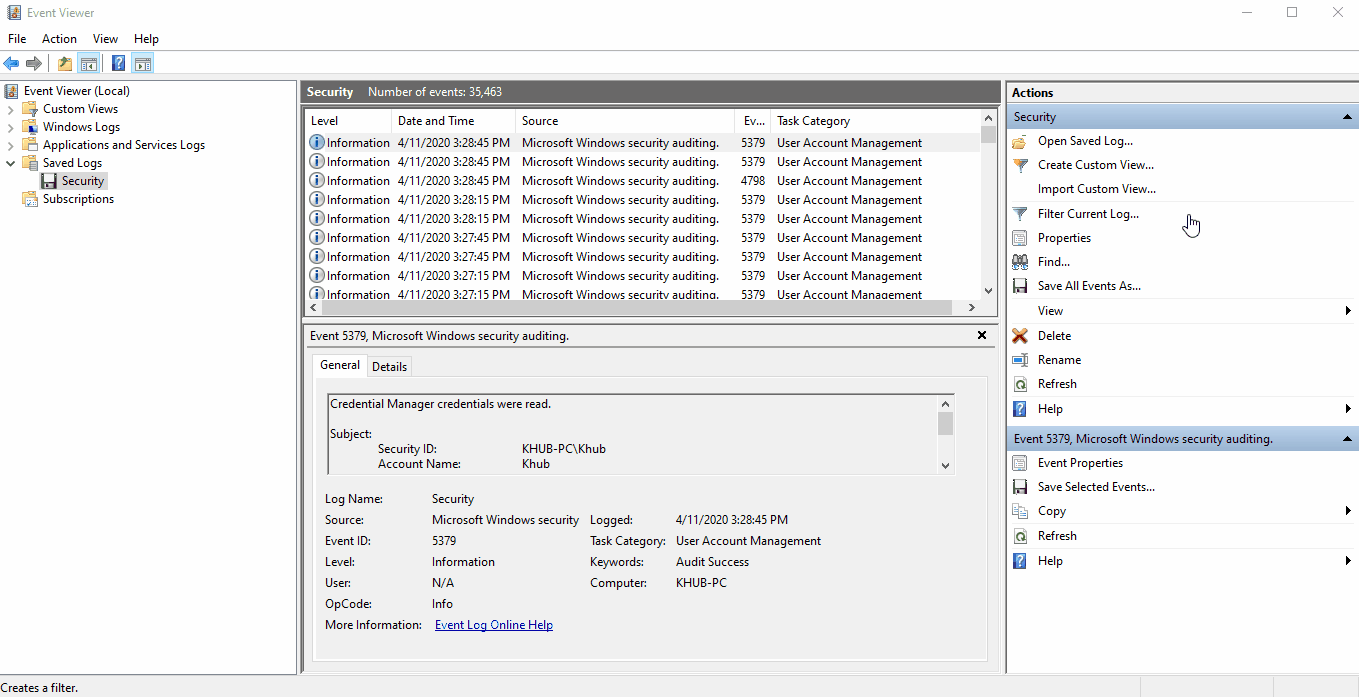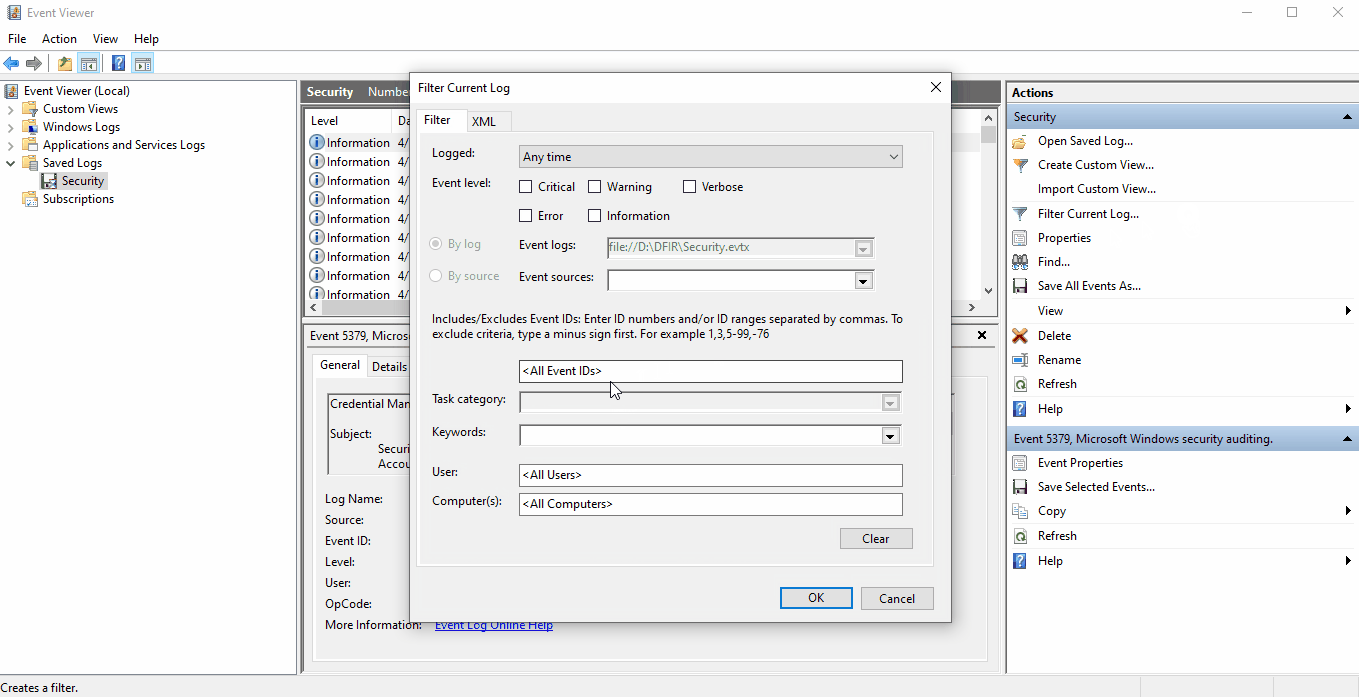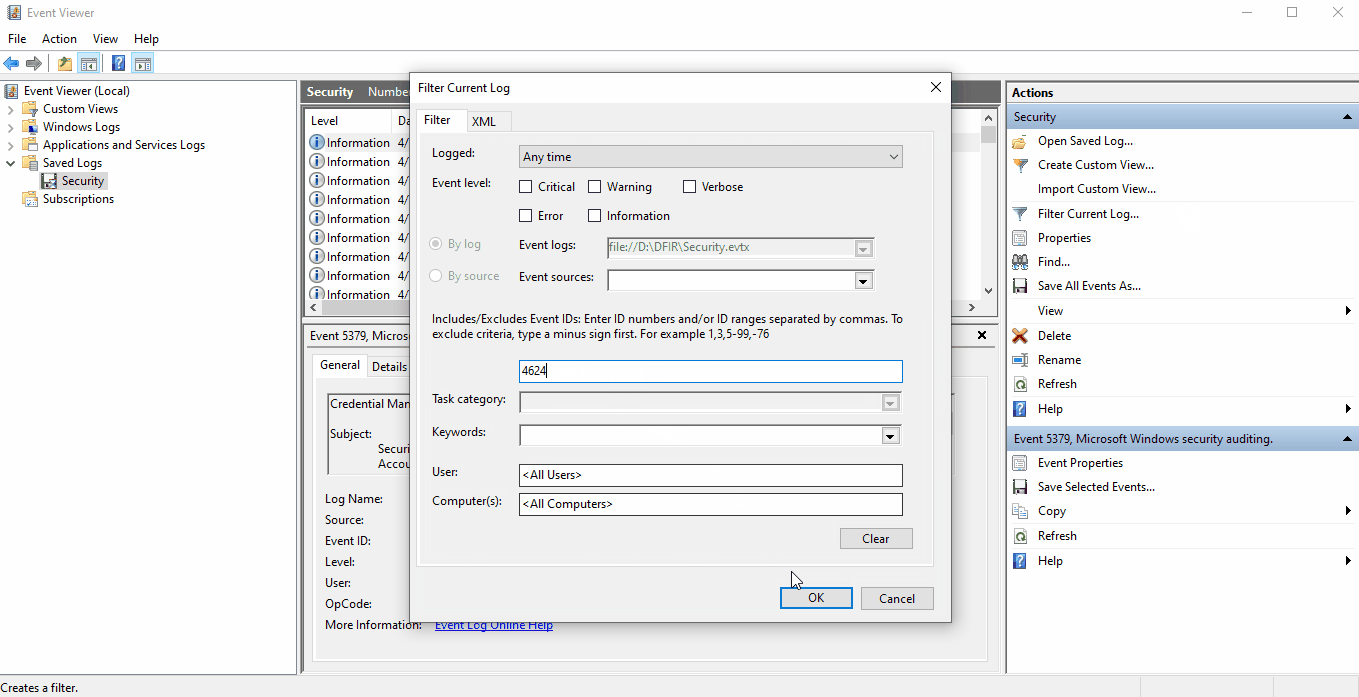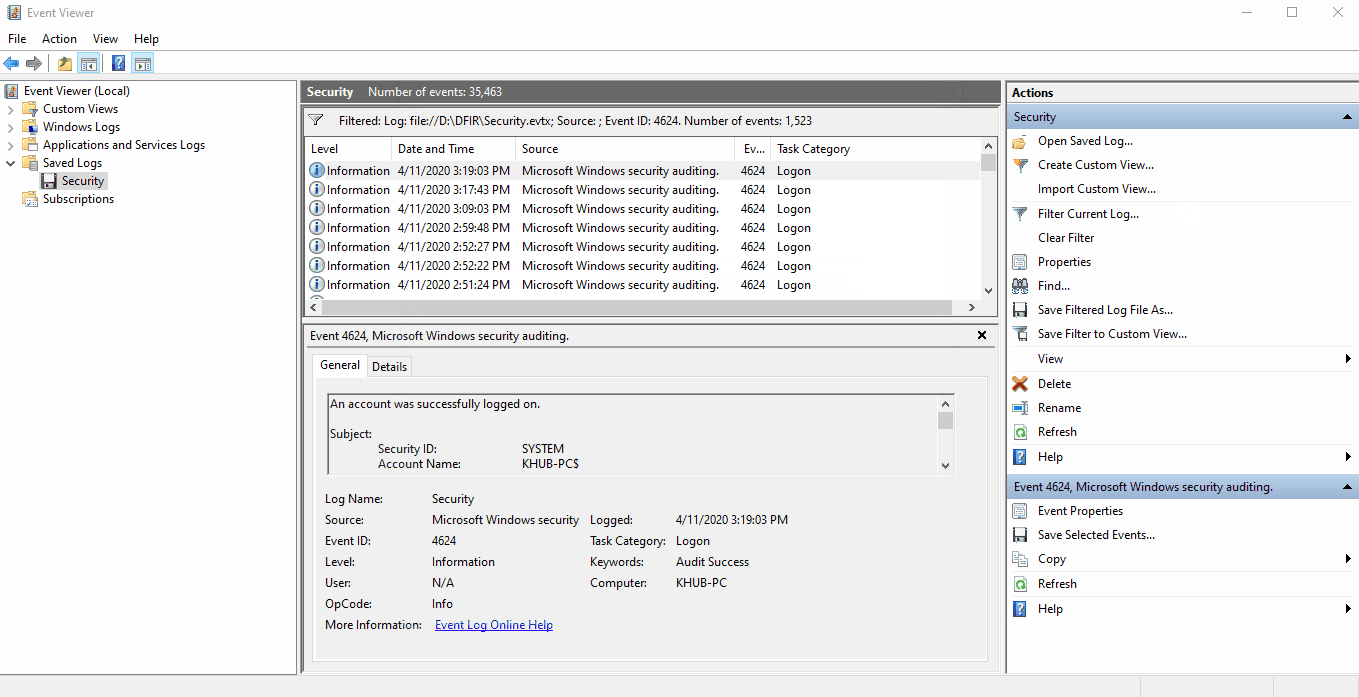
To filter for a specific event, select Filter Current Log... to pull up a dialog box with
filtering option and input the Event ID you'd like to isolate.
I don't currently have any examples of Remote Desktop to showcase, but I'm working on setting up a small
Windows environment for an upcoming Windows Forensics workshop and will capture some examples of RDP. For
some additional reading on RDP, I recommend you check out this Flowchart created by 13cubed, who is an excellent resource within the DFIR community.