This workshop covers the fundamentals of Windows Forensics. Get hands-on experience by capturing a triage image of your own computer and learn about common Windows artifacts.
What you'll learn
- An introduction to Windows Forensics.
- An introduction to key Windows artifacts.
- How to capture a triage image.
What you'll need
- A computer running a Windows Operating System.
- Administrative rights to your computer.
- An Internet Connection.
What is Windows Forensics
Digital Forensics and Incident Response (DFIR) investigation scenarios often revolve around answering a specific question. That's exactly where Windows Forensics comes into play. Windows Forensics is the process of analyzing Windows artifacts to determine what happened in the past.
Why should I learn Windows Forensics?
Whether you're a seasoned veteran within the infosec community or just a computer hobbyist, there is value in understanding how Windows operates and being able to articulate what occurred on an endpoint based on breadcrumbs that are left by the Operating System. After all, Windows doesn't leave artifacts behind to improve the quality of life for forensic analysts, it leaves them behind to improve the user experience. Have you ever wondered how Windows is able to remember the last word document you opened, how it knows to warn you that the file you downloaded was from the Internet, or why that executable seems to run faster the second time you launch it? Windows Forensics will not only teach you about those features, but also teach you how to take advantage of that knowledge to discover events that occurred in the past.
Windows Artifacts
We can classify a Windows artifact as something that can be examined for forensic value. When performing forensics, we don't always need to get a full disk image of the system being analyzed. In-fact, in most circumstances you can get away with only collecting a few key Windows artifacts and you will still be able to answer all the questions necessary to solve your problem.
Windows Registry
The Windows Registry is essentially a database that contains configuration information not only for the underlying Operating System but also for the users that interact with it. Fortunately for us, the data contained within the Windows registry can be easily extracted and analyzed. Without a doubt, it's one of the most important Windows artifacts at our disposal. In this workshop, we'll take a look at how the Windows Registry functions, learn about its core concepts, and most importantly, learn how to take advantage of the data stored within it to conduct our forensic analysis.
Event Logs
Windows keeps track of a variety of status messages for several different applications and services provided by the Operating System. These status messages include errors, warnings, and informational events. If you have ever tried to sift through the seemingly mountains of data within the Windows Event logs, then you may understand why some people who routinely interact with them tend to develop a love/hate relationship. Luckily for us, when conducting forensics, we normally don't have to dive into anything blindly. We're usually trying to answer a very specific question and as a result, we will discuss various methods of using built-in features within the Windows Event viewer to help filter out the noise and quickly identify our needle in the haystack.
Overview
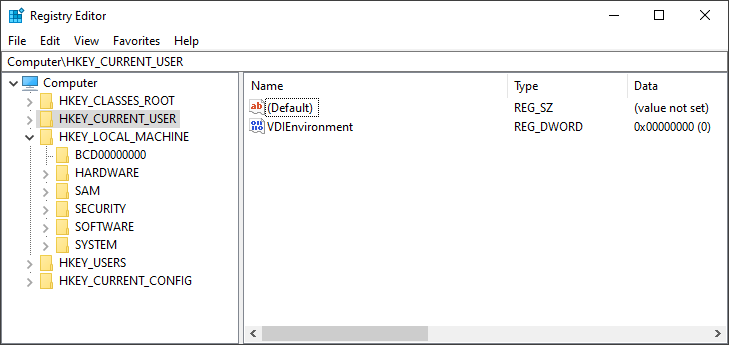
The Windows registry is a hierarchical database that allows applications and system components to store and retrieve configuration data. This data is critical for the operation of Windows and the applications and services that run on Windows. You can access the Windows Registry on a live windows system using regedit.exe.

Keys, Subkeys, and Values
- The registry database is structured in a tree format. [1].
- Each node in the tree is called a key.
- Each key can contain both subkeys and data entries called values.
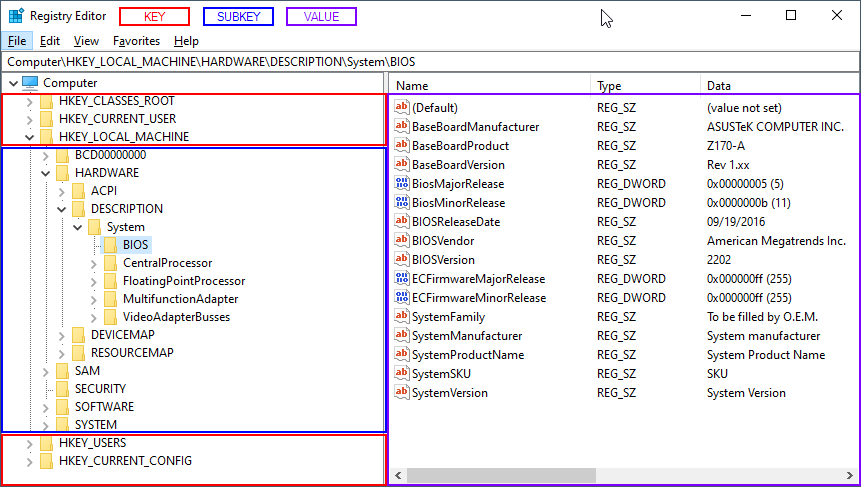
In the image below I've expanded the HKEY_LOCAL_MACHINE (HKLM) key, which contains multiple subkeys with subkeys of their own. I browsed to the HKLM\HARDWARE\DESCRIPTION\System\BIOS key, which contains information related to my workstation's BIOS configuration.
Value Types
The data inside of the Windows Registry can be stored in various formats [2]. Some common data types include:
Value | Type |
REG_BINARY | Binary data in any form. |
REG_DWORD | A 32-bit number. |
REG_QWORD | A 64-bit number. |
REG_SZ | A null-terminated string. |
Keys of Interest
There is a lot of data in the Windows Registry, but these keys in particular contain the most forensic value and are the keys you will be interacting with most.
Registry Key | Data |
HKEY_CURRENT_USER | Configuration Information for the Currently Logged on User. |
HKEY_LOCAL_MACHINE\SAM | Security Account Manager Database |
HKEY_LOCAL_MACHINE\SECURITY HKEY_LOCAL_MACHINE\SOFTWARE HKEY_LOCAL_MACHINE\SYSTEM | Configuration Information for the Workstation. |
In this lab, we're going to explore the Windows Registry on your computer and get a hands-on look at the structure and other common nomenclatures that you will encounter when performing registry forensics. I will ask you to perform a task, followed by a series of questions. Don't worry if you don't know the answer immediately, but try your best to hypothesize the answer. Well review the questions at the end of the lab.
Regedit.exe
Using the run dialog box, open regedit.exe.
Task 1:
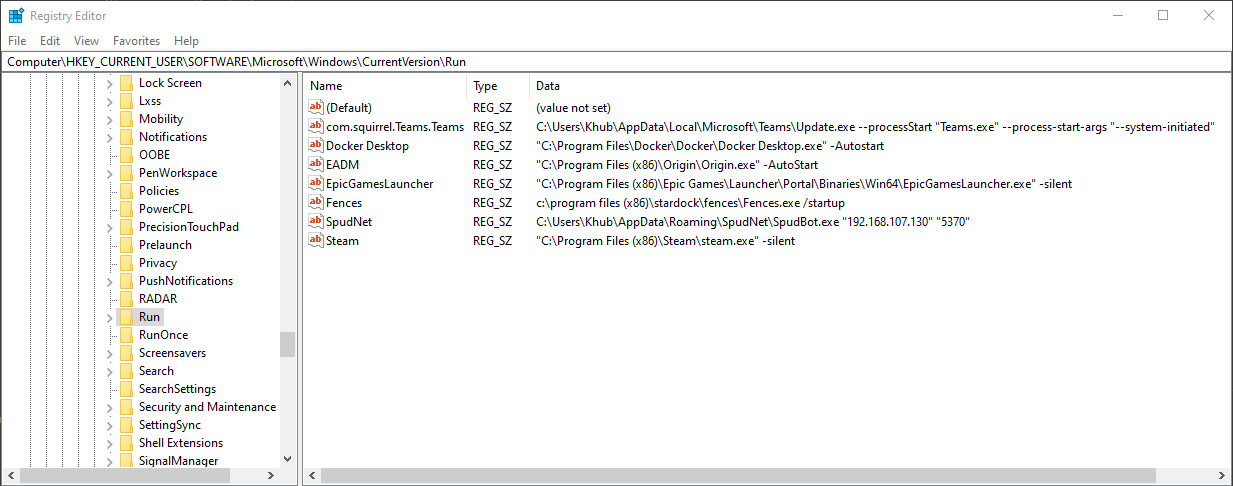
In regedit.exe, navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run.
- What kind of information is stored in this key?
- Is this key referenced each time the computer boots up or each time the currently logged on user logs into the workstation?
Task 2:
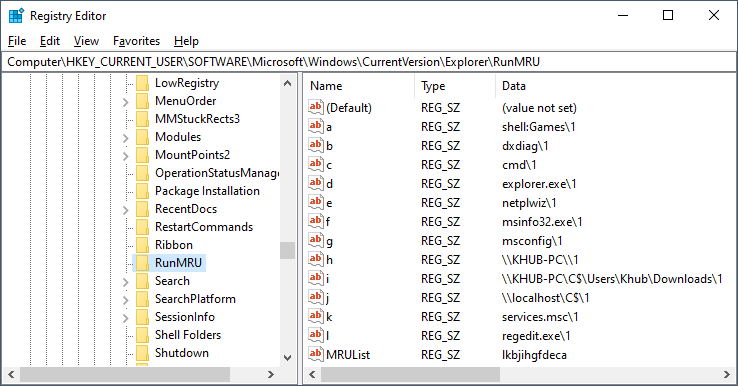
Navigate to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU.
- What information is stored in this key?
- What is an MRUList?
- What was the last command entered in the run dialog box?
Task 3:
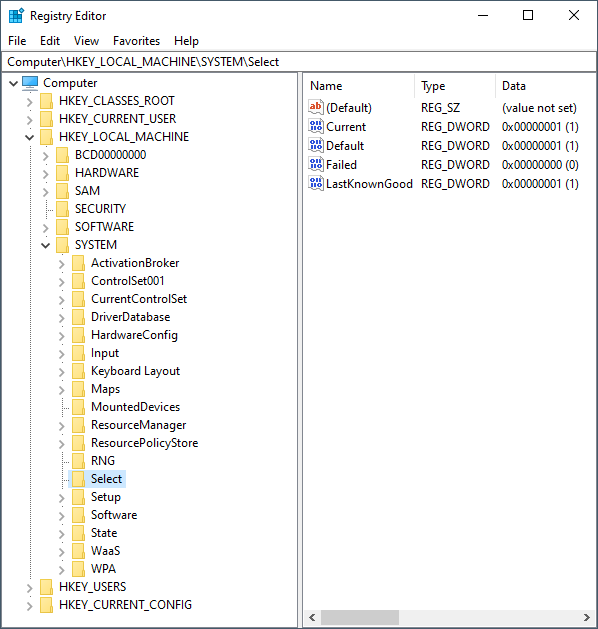
Navigate to HKEY_LOCAL_MACHINE\SYSTEM\Select
- Why is the key valuable?
- Why would a system have multiple ControlSets in place?
Task 4:
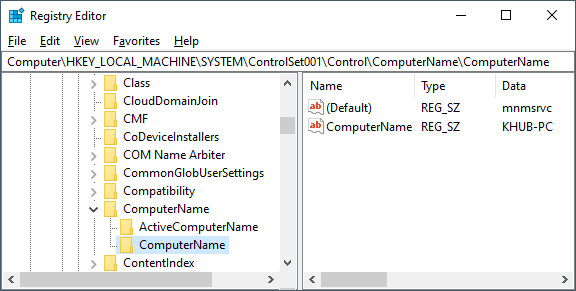
Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
- What value is listed?
- What format is the value listed in?
Task 1 | Review:
This registry location is classified as an ASEP or Auto-Start Extensibility Point and is one of many locations in the registry where data is stored that will execute automatically on Windows start-up. In this case, the data stored in this key will execute whenever the currently logged in user logs into the workstation. It's a legitimate functionality that's often abused by attackers to achieve persistence on a compromised endpoint.
Task 2 | Review:
This key stores strings that have been entered in the run dialog box. This is how Windows is able to keep track of your previous searches when using Run.exe. An MRUList is a concept you will frequently encounter in the registry when working with a value that stores multiple data-points. It stands for Most Recently Used List and keeps track of the order that data has been stored in the key. My MRUList in the screenshot above is: lkbjihgfdeca, meaning that "l" or "regedit.exe" was the last value stored in the key.
Task 3 | Review:
This key stores information about which ControlSet is currently active and being utilized by the Operating System. HKLM\System stores data that's critical for your computer to operate properly, and it's not uncommon to encounter multiple ControlSets such as ControlSet001/ControlSet002, especially when you're performing forensics on older versions of Windows. In those situations you will want to reference HKEY_LOCAL_MACHINE\SYSTEM\Select to identify which ControlSet is active. Why would there be multiple ControlSets? Well, the LastKnownGood key might be a hint. It's to improve system reliability.
Task 4 | Review:
This value lists the Computer Name of the system you're analyzing and is stored in a string format.
Online vs Offline
Thus far, we've discussed how to interact with the Windows Registry on a live system. However, when performing forensics, we're almost never going to be working directly with the system we are analyzing and instead will be working off some type of disk image. So the question is, how can we analyze the registry from an offline system?
Registry Hives
The Windows Registry is actually composed of multiple databases stored on the file system known as Registry Hives. These hives contain the keys, subkeys, and values that make up the Windows Registry and loaded into memory when the operating system is started or when a user logs in. [3]
Registry Hive | Supporting Files |
HKEY_CURRENT_USER | C:\Users\<UserName>\NTUSER.DAT |
HKEY_LOCAL_MACHINE\SAM | C:\Windows\System32\config\SAM |
HKEY_LOCAL_MACHINE\Security | C:\Windows\System32\config\Security |
HKEY_LOCAL_MACHINE\Software | C:\Windows\System32\config\Software |
HKEY_LOCAL_MACHINE\System | C:\Windows\System32\config\System |
In addition to the Registry Hives, there are also some supporting files that you need to be aware of, specifically .log files. .log files are transaction logs that keep track of changes to the keys and values stored in the hive. The corresponding Registry Hives are periodically updated with these changes. These files are located in the same directory next to their corresponding Registry Hive and contain the same name plus the .log file extension. You will need to enable View -> Hidden Items to see them.
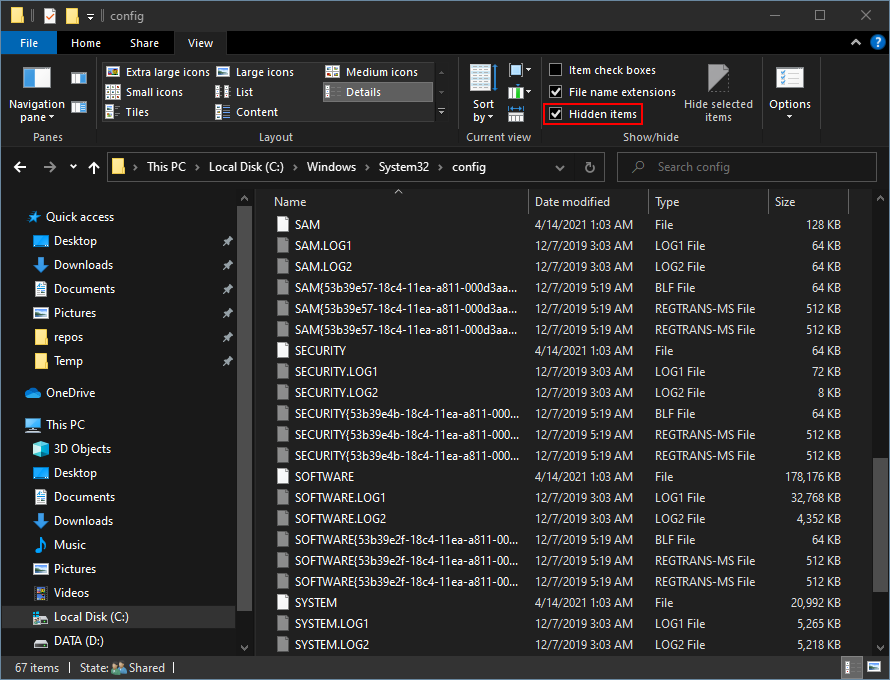
In an upcoming lab, we'll learn about a utility we can use to analyze these files offline.
Overview
Windows utilizes event logging to provide a standard and centralized way for applications and services to record important software and hardware events. The event logging service records events from various sources and stores them in a single collection called an event log. [4] These logs are stored on the file system in %SYSTEMROOT%\System32\winevt\Logs.
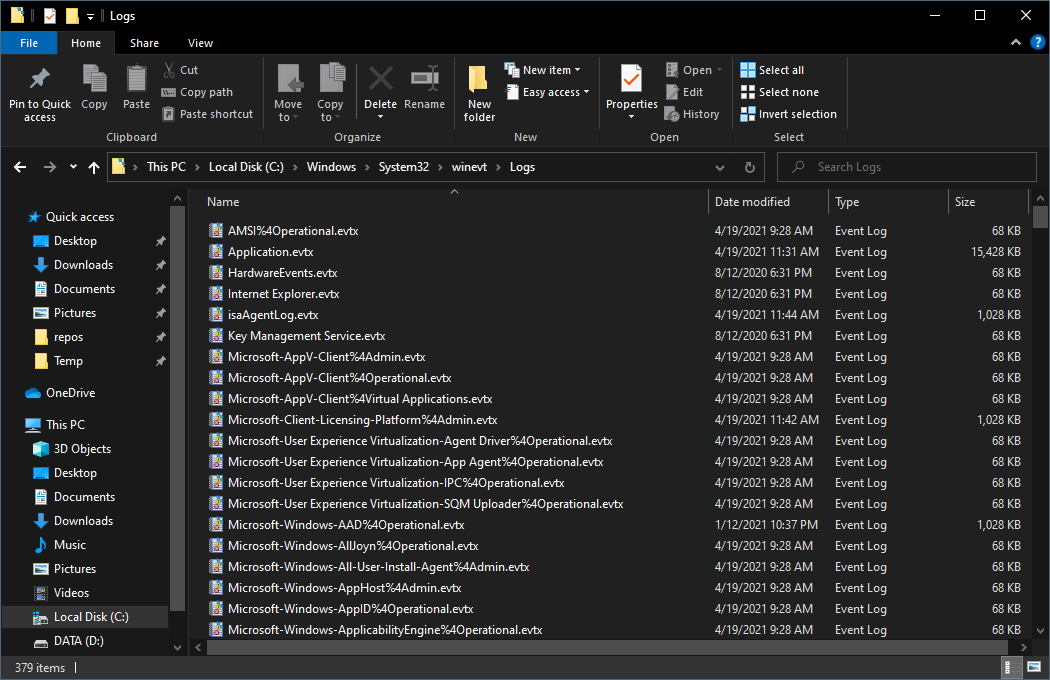
To view these logs on a live system, we can search for Event Viewer in the start menu or enter eventvwr into the run dialog box.
Event Log Structure
When interacting with Windows Event Viewer, you may have noticed that the event logs are structured into two main categories: Windows Logs and Application and Service Logs.
Windows Logs
- Application - The Application.evtx log contains software events logged by applications hosted on the machine.
- Security - The Security.evtx file contains information related to both successful and failed login attempts, in addition to a bevy of other events based on group policy. It's the most frequently referenced event log when performing forensics.
- Setup - The Setup.evtx file contains information related to Windows update.
- System - The System.evtx file contains information related to Windows services and system components. It's very useful when trying to identify that a particular service such as anti-virus was not tampered with during an investigation.
Applications and Services Logs
These logs are often referred to as "Custom Logs". In addition to a variety of useful logs that are baked into a traditional installation of Windows such as logs pertaining to PowerShell, RDP, and Task Scheduler. This is where you can point your custom application to store logs.
Event Types
Before we jump into the lab, it's important to understand what types of events are logged. Understanding the type of event will help you interpret whether or not the action was successful. [5]
Event Type | Description |
Warning | An event that is not necessarily significant, but may indicate a possible future problem. For example, when disk space is low, a Warning event is logged. If an application can recover from an event without loss of functionality or data, it can generally classify the event as a Warning event. |
Information | An event that describes the successful operation of an application, driver, or service. For example, when a network driver loads successfully, it may be appropriate to log an Information event. Note that it is generally inappropriate for a desktop application to log an event each time it starts. |
Success Audit | An event that records an audited security access attempt that is successful. For example, a user's successful attempt to log on to the system is logged as a Success Audit event. |
Failure Audit | An event that records an audited security access attempt that is successful. For example, a user's successful attempt to log on to the system is logged as a Success Audit event. |
As we discussed earlier in our workshop, we don't need to capture a full disk image to perform forensics. In this lab, we're going to use a fantastic utility: Kroll's Artifact Parser and Extractor (KAPE) to capture a triage image.
To get started, register with KROLL to download KAPE via the link below:
Once downloaded, unzip the downloaded file and execute the GUI version of KAPE: gkape.exe.
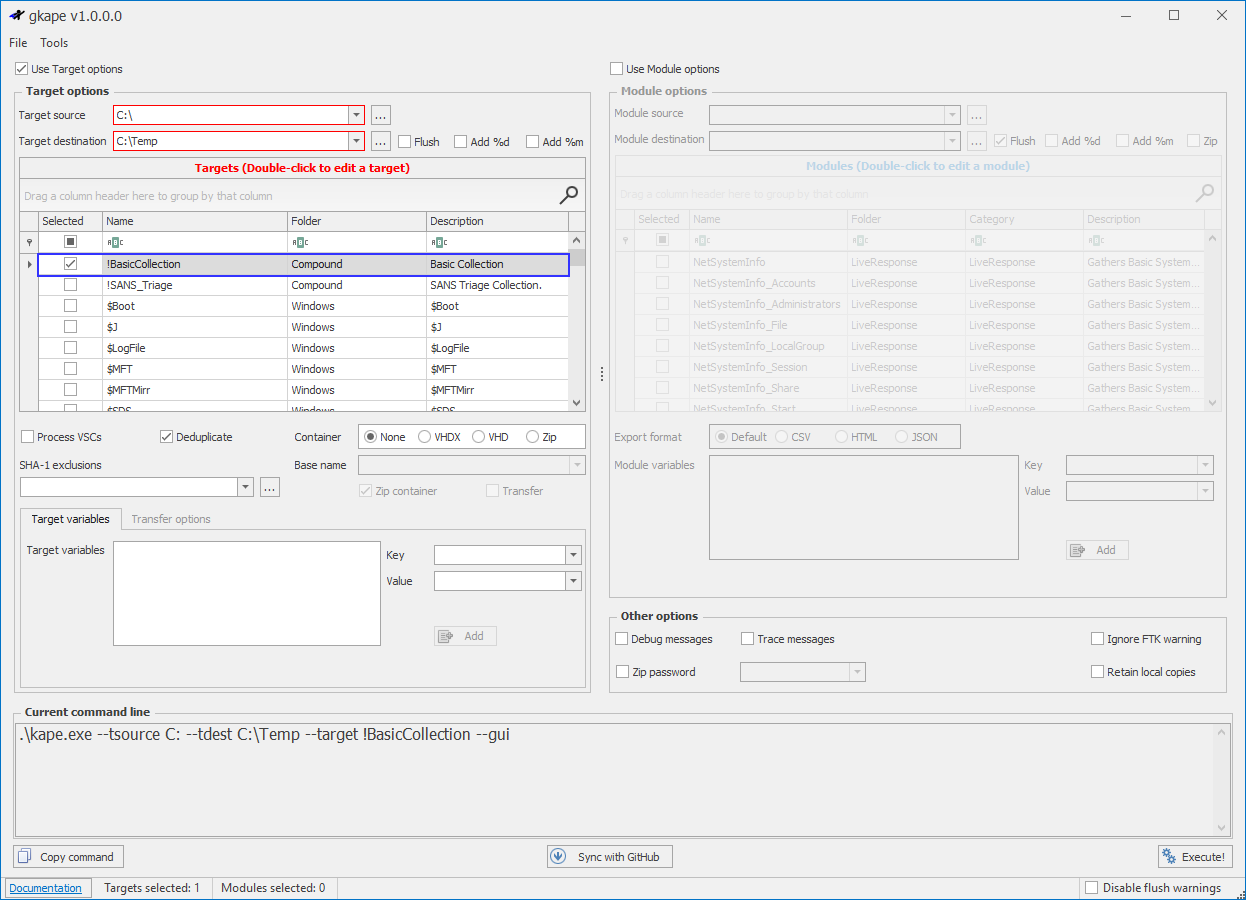
To capture a triage image with KAPE:
- Select the checkbox for Use Target options.
- Select the ellipsis next to Target source and select the root of your Operating System.
- Select the ellipsis next to the Target destination and select a folder to output your triage image.
- Make sure to uncheck Flush in order to avoid wiping your destination directory.
- In the Targets window, select !BasicCollection.
- Select Execute to kick off the triage image.
In this lab, we're going to review Windows event logs within Event Viewer to get a better understanding of how to query for specific events of interest and how to properly interpret them. Specifically, we will walk through some of the more frequent windows authentication events that are most likely to be relevant in a forensic investigation.
Task 1: Can we identify your last Console logon?
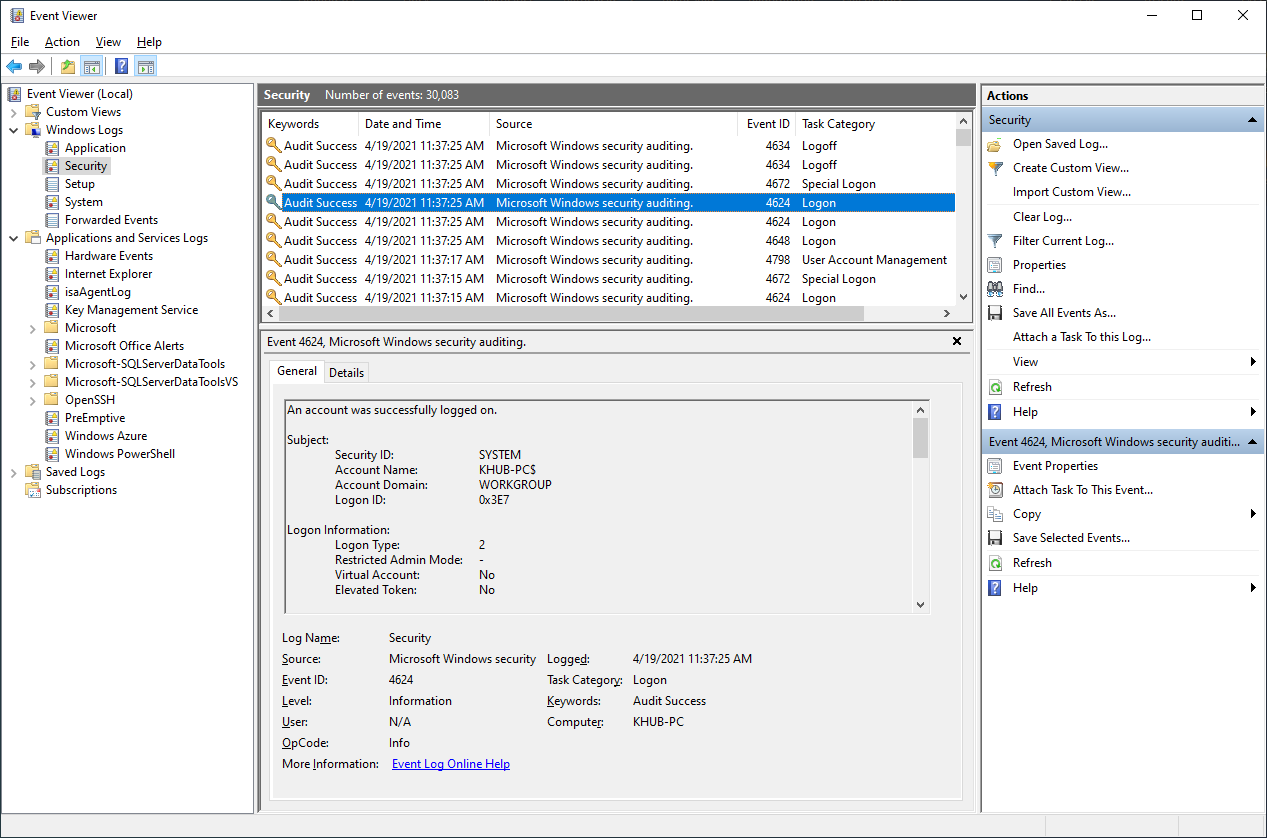
Windows logon events can give us very specific information regarding the nature of account authorizations on a system, presuming that we know where to look and how to decipher the logs. In addition to telling us the Date, Time, Username, Hostname, and Success/Failure status of an attempted logon, we can also determine exactly how a logon was attempted.
Within Windows Explorer, browse to the output directory from your KAPE triage image and double-click the Security.evtx file from C:\Windows\System32\winevt\logs\. The Security.evtx logs should automatically be opened with the Saved Logs section of Event Viewer. You can replicate this method to analyze any offline .evtx file.
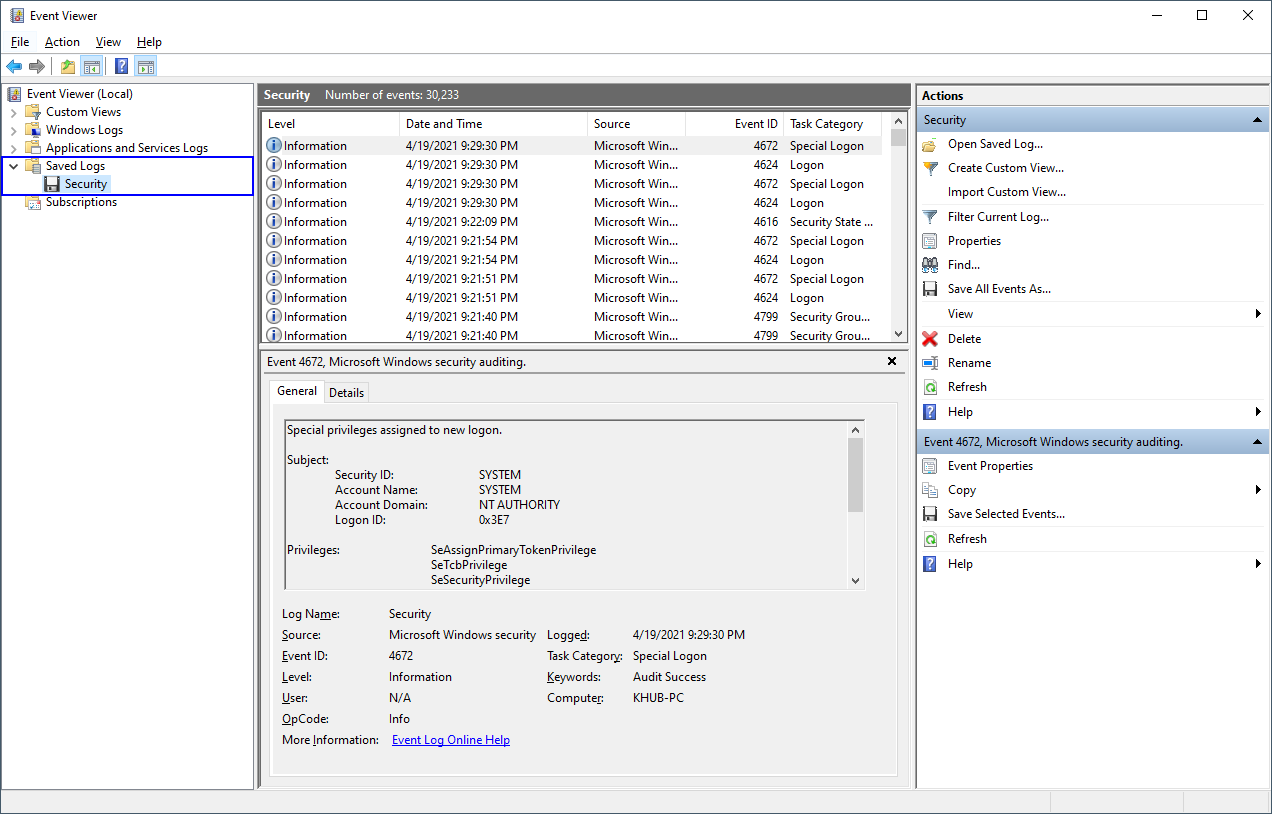
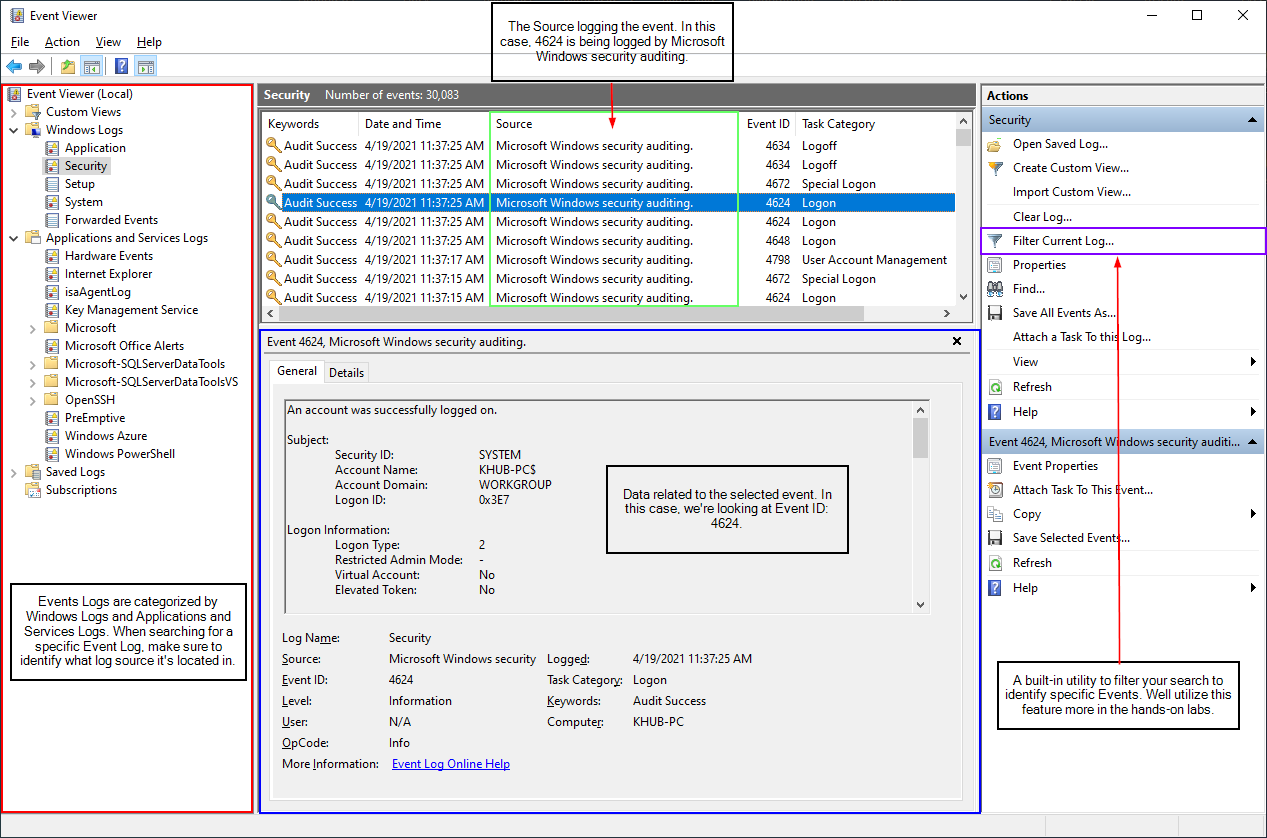
Select the newly imported Security log within Event Viewer and then select Filter Current Log ... to narrow your results to only show Event ID: 4624.
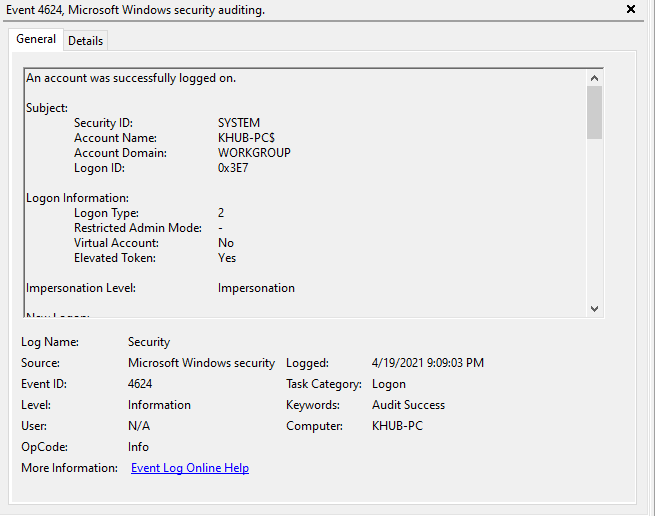
Browse through the results and try to familiarize yourself with the event. Windows generates a 4624 event for every successful logon attempt to the local computer. You might notice this event isn't limited to only your user account. There are numerous other authentication events that happen behind the scenes, particularly from Windows service logins.
In order to find the last time you logged into your workstation via the console, as in directly logging into your computer from a keyboard/mouse. We're going to have to identify a specific Logon Type. As I briefly highlighted in the introduction of this task, a 4624 event doesn't just capture who logged in, but it also gives us some insight into how someone logged in. Below is a table listing out the different types of login's tracked by 4624.
Logon Type | Explanation |
2 | Logon via Console |
3 | Network Logon |
4 | Batch Logon |
5 | Windows Service Logon |
7 | Credentials used to Unlock Screen |
8 | Network Logon sending Credentials |
9 | Different Credentials used than Logged on User |
10 | Remote Interactive Logon (RDP) |
11 | Cached Credentials used to Logon |
12 | Cached Remote Interactive (Similar to Type 10) |
13 | Cached Unlock (Similar to Type 7) |
Scroll through the list of 4624 events and see if you are able to identify any console logins for your user account. If not, what kind of login types were you able to find?
For more information on this particular event in addition to more advanced tips and tricks for filtering your results. I encourage you to check out this entry within my Windows Artifact Database: https://windowsforensics.net/database/account-usage/logon-types.html.
Task 2: Are you as bad at Typing as me?
We learned how to analyze successful logins, but what about the bad ones?
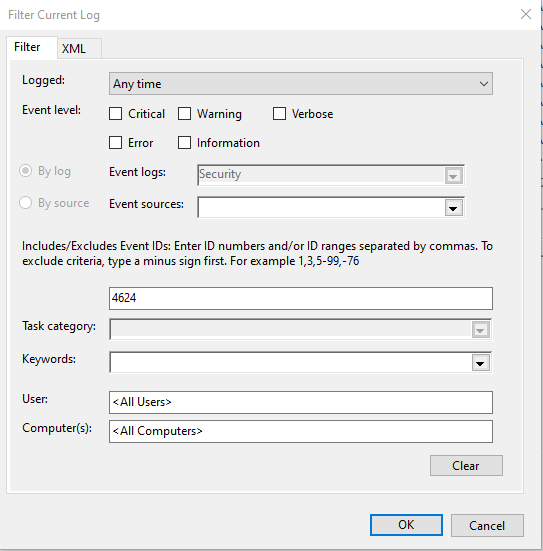
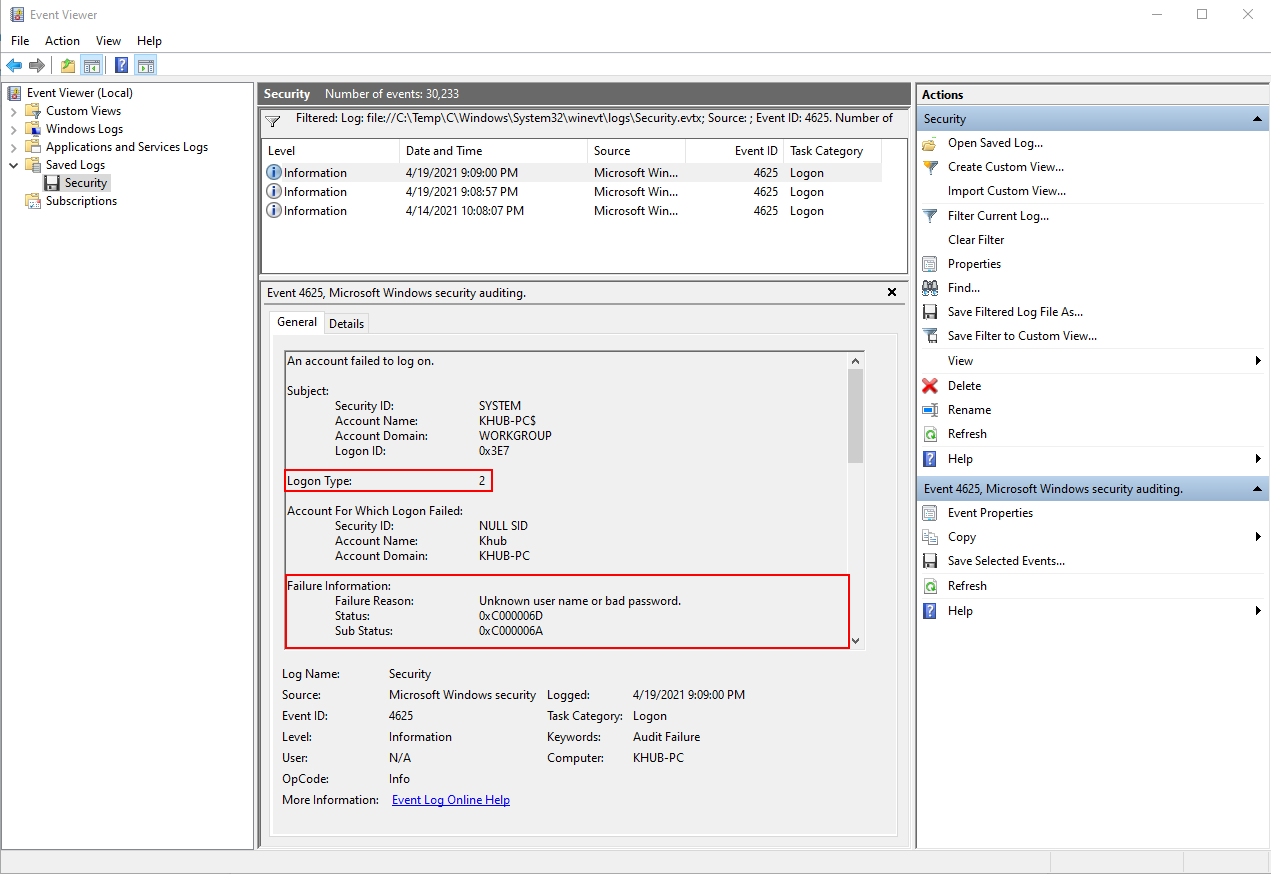
Select the recently imported Security log within Event Viewer and then select Filter Current Log ... to narrow your results to only show Event ID: 4625.
This event logs unsuccessful logon attempts. In addition to providing us with a Logon Type, it also provides us with a status code, detailing the failure reason. For more information on how to interpret these status codes, I recommend bookmarking https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/ in your web browser of choice. The author of this website has created an excellent knowledge base documenting various Windows security log events, and it's my go-to resource when wanting additional context on what a particular event is telling me.
In my example below, the Failure Reason states that my login failed either due to a bad username or a bad password. To find out exactly why it failed, we have to translate the hexadecimal Status and Sub Status codes. To do this, reference Ultimate Window Security's research on Event ID: 4625.
In this lab, we're going to learn how to analyze extracted Registry Hives. To get started, download and unzip the latest version of Registry Explorer from Eric Zimmerman.
We're going to use the GUI utility Registry Explorer.exe to analyze your extracted hives. To get started:
- Open up Registry Explorer.exe.
- Select File.
- Select Load hive in the dropdown menu.
- Navigate to the output directory from your KAPE triage image and select the hive you would like to analyze.
- You will likely encounter a warning message if there is uncommitted data in the transaction logs. Don't worry, this is normal. Remember that these Registry Hives are protected Operating System files and data is routinely written to transaction log files before being uploaded to the main Registry Hive.
- Select Yes then Ok to replay the transaction logs.
- Use the <Ctrl> key to select all of the relevant .log files for the Registry Hive you're analyzing and select Open.
- Registry Explorer will then ask you to save the newly created hive file. Select OK and choose a location to output the updated hive file.
- Select Yes to load the updated hive.
- You may be asked another time if you would like to load the original dirty hive you selected. Select No and your hive will load in a few seconds.
Similar to the other labs in this workshop, I'm going to ask you to perform a task, followed by a series of questions. In this case, we will be reviewing different artifacts in the registry and will start to put together a better idea about how useful the Windows Registry can be when performing forensic analysis. Don't worry if you are unable to answer all of the questions. We will review each task at the end of the lab.
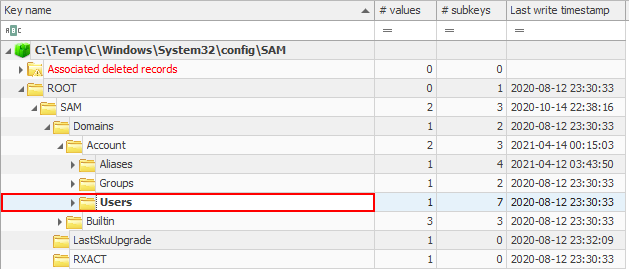
Task: Exploring the SAM Database
In Registry Explorer, load the SAM hive and navigate to: SAM\Domains\Account\Users.
- What user accounts are listed in your SAM database?
- How many times have you logged onto your user account?
- When did you last reset the password for your user account?
- When was the last time you entered an incorrect password during a Windows logon?
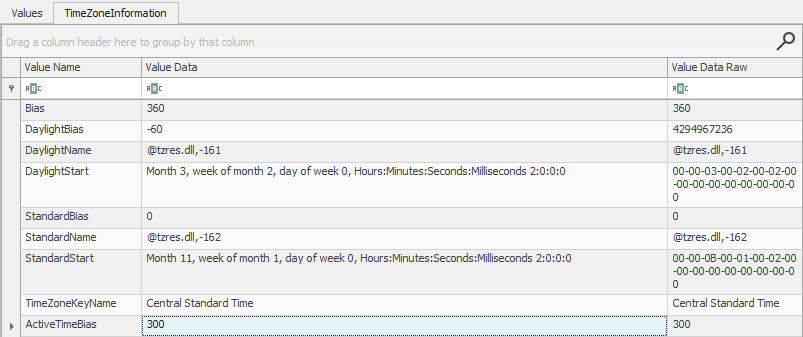
Task: Anybody got a Watch handy?
In Registry Explorer, load the SYSTEM hive and navigate to SYSTEM\CurrentControlSet\Control\TimeZoneInformation.
- What is the display name of your computer's registered time zone?
- What is the decimal value of ActiveTimeBias?
- What does ActiveTimeBias calculate for you?
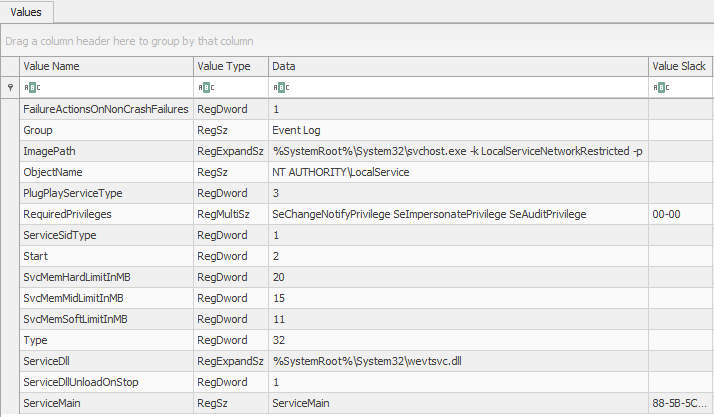
Task: How may I Serve you?
Within the SYSTEM hive, navigate to SYSTEM\CurrentControlSet\Services.
- Compare the data at this location in Registry Explorer with the same data in regedit.exe. Can you identify what Registry Explorer is doing to simplify your analysis?
- Expand the Services key and search for the EventLog key. What is the decimal value of Start and what does that value represent?
Task: How Long have I been Here?
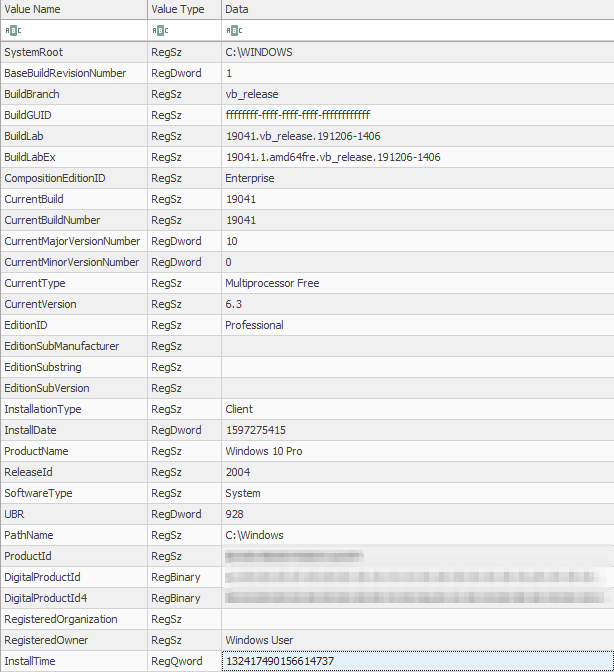
In Registry Explorer, load the SOFTWARE hive, navigate to SOFTWARE\Microsoft\Windows NT\CurrentVersion.
- What is the value of ProductName?
- What build of Windows are you running?
- What edition of Windows are you running?
- Can you figure out how to convert the value of InstallTime to identify what date the Operating System was installed?
Task: What's the WiFi Password?
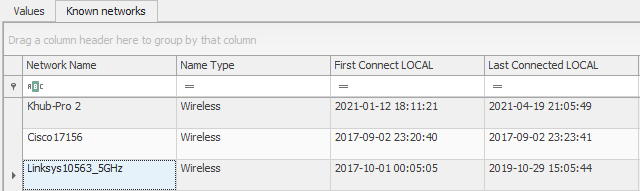
Within the SOFTWARE hive, navigate to SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList.
- When is the last time your PC was connected to your home network?
- What is the First Network your device was connected to?
- Browse the Subkey's underneath SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles. Is Registry Explorer making our lives easier again?
Task: Who needs Cortana?
In Registry Explorer, load the NTUSER.DAT hive, navigate to NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQuery.
- What is the last thing you searched for?
- Scroll through the results, do you remember searching for any of the listed values in particular?
- What could this tell you in a forensic investigation?
Task: Did you open that Super Secret File?
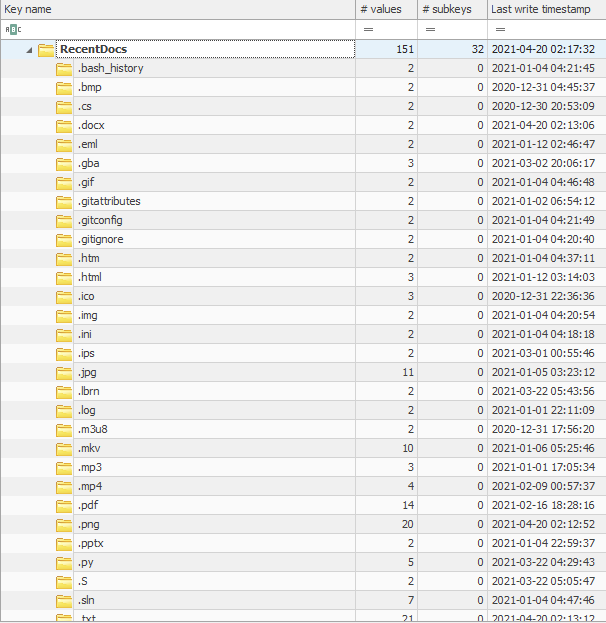
Within the NTUSER.DAT hive, navigate to NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs.
- Based on the data, what do you think this key is keeping track of?
- How is the data within the output of the Recent documents plug-in sorted?
- Expand the subkeys underneath NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs. What is the last .pdf file you opened?
- Review the NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.zip key. Can you identify the late time you interacted with a .zip file?
- Review this key in regedit.exe. What is the value of the first entry in the MRUList?
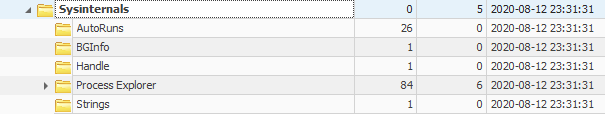
Task: Who is Mark Russinovich?
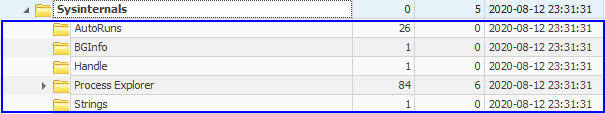
Within the NTUSER.DAT hive, navigate to NTUSER\Software\Sysinternals.
- Have you executed any Windows System Internals tools?
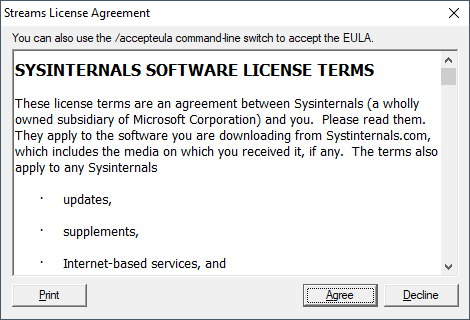
- If so, drill down into any one of the subkeys and answer the following question. What's the value of EulaAccepted?
Task: Saving the Best for Last
Before we close out this workshop. I want to showcase a quality of life feature within Registry Explorer that you can utilize to speed up your future investigations. With your Registry Hives still loaded, select the Available bookmarks tab. The majority of these keys are leveraging plug-ins to parse the data and present it in a more easily digestible format. This feature allows you to quickly locate keys of forensic interest. Before you finish this workshop, browse through some of the keys and take notes on anything that captures your interest!
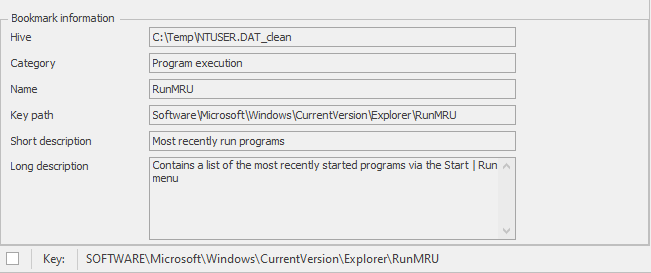
Task Review | Exploring the SAM Database
The Security Account Manager (SAM) is a database that is present on computers running Windows operating systems that stores user accounts and security descriptors for users on the local computer. [6] Registry Explorer utilizes a plug-in to populate the SAM\Domains\Account\Users key with all the information we need to conduct our analysis and profile the local users on the workstation.
- What user accounts are listed in your SAM database?
- The SAM hive should contain information about every local user account that's present on the computer.
- How many times have you logged onto your user account?
- The Total Login Count field shows the decimal value for the number of logins.
- When did you last reset the password for your user account?
- The Last Password Change field shows the Date/Time stamp for when your password was last modified. For more information regarding this artifact, reference this entry in my Windows Artifact Database: https://windowsforensics.net/database/account-usage/last-password-change.html.
- When was the last time you entered an incorrect password during a Windows logon?
- The Last Incorrect Password field shows the Date/Time stamp for the last time someone attempted to log into your user account with the wrong password.
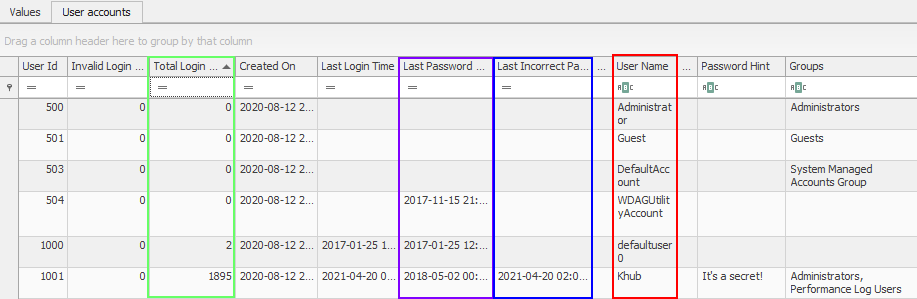
Task Review | Anybody got a Watch handy?
The SYSTEM\CurrentControlSet\Control\TimeZoneInformation key keeps track of the computer's time configuration settings. It's always a good idea to identify local time on a system before conducting your analysis to ensure that you're capturing the proper timestamps during an investigation. After capturing the local timestamp, you need to identify whether your tools are displaying local time or taking it upon themselves to automatically convert the local timestamp to UTC.
- What is the display name of your computer's registered time zone?
- The string value of TimeZoneKeyName lists the display name of your computer's registered time zone.
- What is the decimal value of ActiveTimeBias?
- This value is located in the ActiveTimeBias key.
- What does ActiveTimeBias calculate for you?
- The ActiveTimeBias key lists the +/- minutes value of your computer's local timezone compared to UTC. For example, my workstation is set to Central Standard Time which is 5 hours behind UTC. So my ActiveTimeBias is set to 300, since my workstation is 300 minutes behind UTC.
Task Review | How may I Serve you?
The SYSTEM\CurrentControlSet\Services key keeps track of Windows Services and their configuration details.
- Compare the data at this location in Registry Explorer with the same data in regedit.exe. Can you identify what Registry Explorer is doing to simplify your analysis?
- As you may have already discovered, Registry Explorer leverages various plug-ins to parse the registry and simply our analysis. When you view the SYSTEM\CurrentControlSet\Services in Registry Explorer, a plug-in enumerates all of the subkeys and populates the key with all of the data we need to perform our analysis. However, when analyzing that same key in regedit.exe, you can see that the SYSTEM\CurrentControlSet\Services is actually empty and all the relevant data is stored within the underlying subkeys.
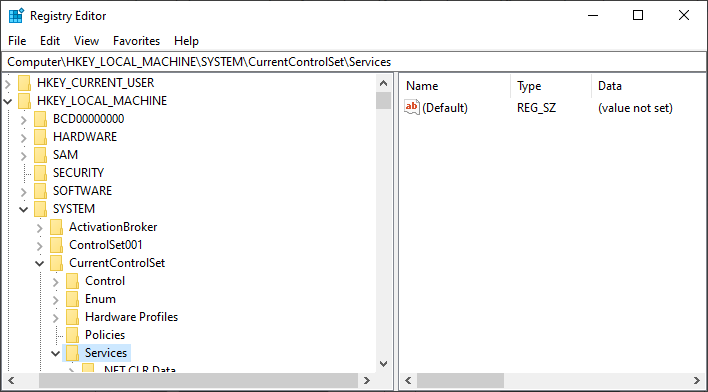
- Expand the Services key and search for the EventLog key. What is the decimal value of Start and what does that value represent?
- The decimal value is most likely 2. You can determine what that value represents in multiple ways. If you google: "services start decimal value", you will find multiple blog posts informing you that a value of 2 indicates that the service will startup automatically. Alternatively, if you go back to SYSTEM\CurrentControlSet\Services and search the output from Registry Explorer's TimeZoneInformation plug-in. There will be a field named Start Mode that will say Automatic, since it's doing the decimal interpretation for you.
Task Review | How Long have I been Here?
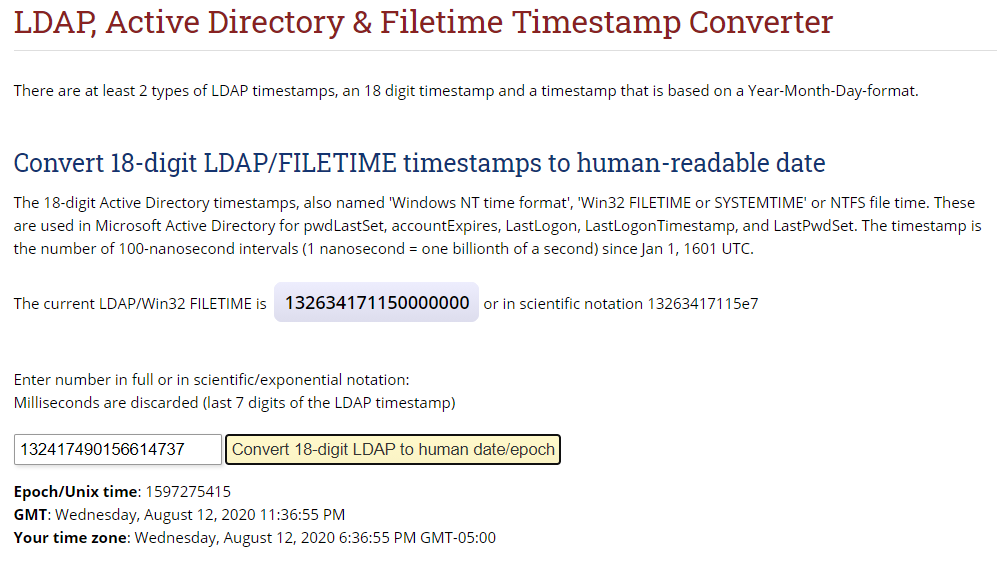
The SOFTWARE\Microsoft\Windows NT\CurrentVersion key contains information about the Windows installation, including key details such as the Operating System install date, version number, build number, etc.
- What is the value of ProductName?
- The ProductName key will list what Operating System your computer is running.
- What build of Windows are you running?
- You can identify what specific version of Windows you are running by referencing the CurrentBuild key.
- What edition of Windows are you running?
- The EditionID key will list what edition of Windows you are running.
- Can you figure out how to convert the value of InstallTime to identify what date the Operating System was installed?
- The InstallTime field lists the Date/Time stamp for when the Operating System was installed. This field is stored in LDAP/Win32 time. You can utilize https://www.epochconverter.com/ldap to convert the timestamp to a human-readable format.
Task Review | What's the WiFi Password?
The SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList contains information about what networks your computer has connected to.
- When is the last time your PC was connected to your home network?
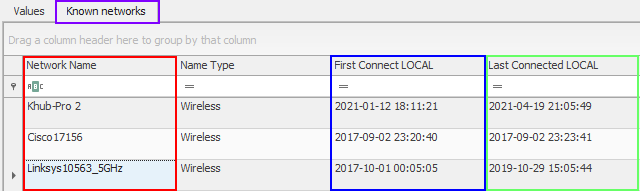
- After identifying your home network. You can reference the Last Connected LOCAL to capture the Date/Time that your workstation was last connected.
- What is the First Network your device was connected to?
- The easiest way to determine this is to take advantage of Registry Explorer's sorting feature, and select the First Connect LOCAL field to sort by Date/Time from earliest to latest.
- Browse the Subkey's underneath SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles. Is Registry Explorer making our lives easier again?
- Once again, a Registry Explorer plug-in is doing most of the heavy lifting. Browsing through the subkeys of SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles will showcase that Registry Explorer is enumerating data to populate the Known networks plug-in.
Task Review | Who needs Cortana?
The NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQuery keeps track of keyword searches in Windows. As highlighted in the original task: In Windows 7, the WordWheelQuery keeps track of keyword searches from the start menu.
In Windows 10, the WordWheelQuery keeps track of searches within Windows Explorer. For more information regarding this artifact, reference this entry in my Windows Artifact Database: https://windowsforensics.net/database/file-knowledge/search-wordwheelquery.html.
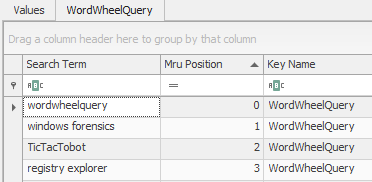
- What is the last thing you searched for?
- This key will either track keyword searches from the start menu or searches within Windows Explorer depending on what version of Windows you happen to be running.
- Scroll through the results, do you remember searching for any value in particular?
- This task is self-explanatory, but a fun side quest for you to attempt would be to test out this key for yourself in real-time. Depending on your Operating System, perform a keyword search in the Windows Start Menu or Windows Explorer respectively. Then analyze the key using regedit.exe to see if your action left any artifacts behind.
- What could this tell you in a forensic investigation?
- This artifact could be leveraged to prove that a user had knowledge about something. For example, if you were performing an investigation and asked to identify whether or not a user was aware about a particular file in question. Since this artifact is triggered only under unique circumstances, the absence of it one way or another isn't unusual. However, it's something you should understand so that you can leverage it when the opportunity arises.
Task Review | Did you open that Super Secret File?
The NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs key will track the last files and folders opened and is used to populate data in "Recent" menus of the Start menu. For more information regarding this artifact, reference this entry in my Windows Artifact Database: https://windowsforensics.net/database/file-folder-opening/recent-files.html.
- Based on the data, what do you think this key is keeping track of?
- This key is keeping track of files/folders that were recently accessed. The data from this key is also stored in %APPDATA%\Microsoft\Windows\Recent.
- How is the data within the output of the Recent documents plug-in sorted?
- The data within this plug-in is sorted by MRU position.
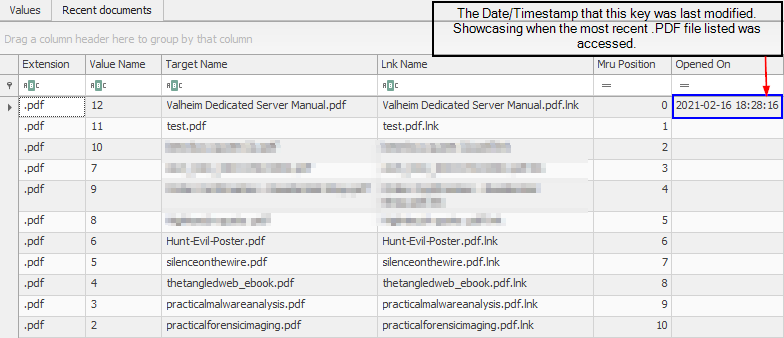
- Expand the subkeys underneath NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs. What is the last .pdf file you opened?
- While the RecentDocs key will last the last 150 files/folders accessed. You can drill down into the subkeys which are sorted by extension to identify files for a specific file extension.
- Review the NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.zip key. Can you identify the late time you interacted with a .zip file?
- The Last write timestamp of the NTUSER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs\.zip key can be referenced to identify the last time that a .zip file was accessed. This technique can only be leveraged to identify the Date/Timestamp for the file that was most recently accessed per extension, since the value is updated each time the key is modified.
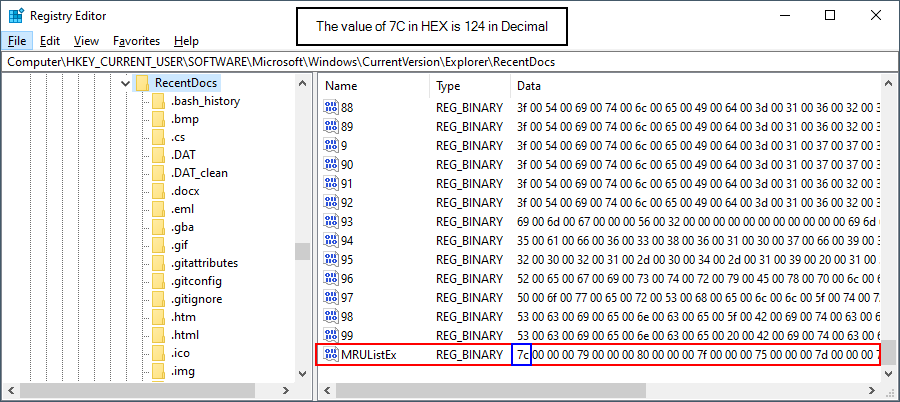
- Review this key in regedit.exe. What is the value of the first entry in the MRUList?
- When viewing this key in regedit.exe, it's very likely that you will need to convert the HEX value of the MRUList into decimal format in order to correctly identify which file/folder was last accessed.
Task Review | Who is Mark Russinovich?
The NTUSER\Software\Sysinternals is a unique registry key that keeps track of different properties regarding the Windows Sysinternals tool suite. You can learn more about Windows Sysinternals here: https://docs.microsoft.com/en-us/sysinternals/. This key can be very valuable during a forensic investigation as attackers are more commonly starting to leverage a technique classified as Living off the Land. Relying on trusted applications and protocols that are already commonly utilized in your environment to exploit your network as opposed to uploading custom tools.
- Have you executed any Windows SysInternals tools?
- This key will only be present if you have executed a tool from Windows SysInternals. If you have, then the tool you executed will be listed as a subkey of NTUSER\Software\Sysinternals.
- What's the value of EulaAccepted?
- The majority of SysInternals utilities will require the user to accept a Eula before executing. This field captures whether or not the Eula was accepted.
Task Review | Saving the Best for Last
You have to learn how to walk before you run is an idiom that you will experience first hand over and over in the field of Cyber Security. As you continue your pursuit of knowledge and learning about more and more tools that make your life easier along the way. I encourage you to keep asking questions to ensure that you understand the core concepts about how something functions behind the scenes even as various tools/utilities continue to emerge that make your life as a forensic investigator easier and easier.
Congratulations, you've successfully completed your first Windows Forensics workshop!
You received a sneak peak at the art of Windows Forensics, but this tutorial was only scratching the surface. I encourage you to take your new found skills and continue your pursuit of knowledge. Be on the lookout for additional tutorials coming in the near future.
What's next?
Now that you have a basic understanding of Windows Forensics, I encourage you to check out my Windows Artifact Database and experiment with additional forensic techniques using the triage image you captured in this workshop.